SOAR - Use Cases
-
ChatGPT integration
Im trying to integrate chatgpt with logpoint and the chatgpt plug in files that i found on the logpoint website are json files. When I tried upladoing them it says that logpoint plugins font support json files. Has anyone been in a similar situation and/or know what to do.
Thankyou -
Why this error message ?
Hi,
I am trying to create a playbook in order to block an account. However I have an error message thas I can’t undrestand the reason.
Could you please tell me why I have this error message ?
“Bad/missing Action inputs! Details: Bad rest-action url: /users/...”
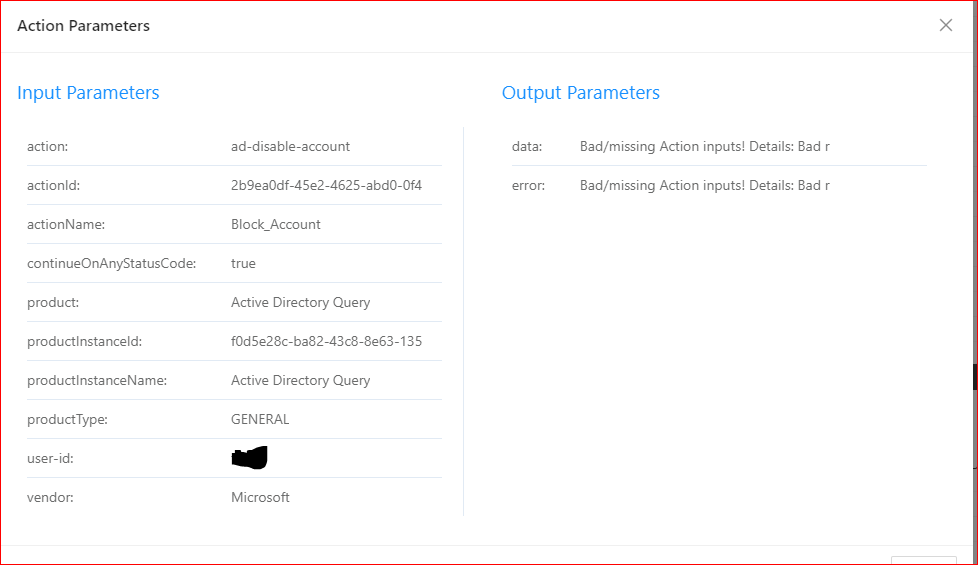
Thank you in advance.
Regads,
Siawash
-
SOAR Playbook Creation From LogPoint Alerts
Hi,
I need your help regarding the SOAR. In fact, I have just started the SOAR and I want to create a playbook From LogPoint alerts in order to block an IP@ or an action. Could please help me ? How can I do that ?
Thank you in advance.
Regards,
Siawash
-
How to configure AbuseIPDB instance in LogPoint SOAR
Hi everyone,
I need to check some source addresses in my playbooks and I want to use AbuseIPDB for this action, but I can’t finish configuring AbuseIPDB instance and obtain some errors. Could you help me with the correct configuration for this instance in SOAR LogPoint Playbook integrations?. I have my api_key but I don’t know what is the correct base_url and threshold parameters if I need to review IP address.
I hope your help
Regards
Gabriel
-
Launch a playbook when an alert is triggered
l have an alert rule that triigers when it detects a web attack like XSS, SQLI.
i want my playbook to starts when the alert is triggered.
Any idea??
-
A playbook that streamlines the process of investigating incidents associated with a specific IP address
Hey everyone,
During my day to day, I identified a workload that I was able to fully automate with SOAR playbook.
I have created a SOAR playbook that does the following.
Takes the outbound IP address from incident data as a trigger. In my example, 213.183.58.12.
The playbook automates the following workload.
- Checks WhosthisIP to gather information about this external IP (domain, etc)
- Uses SearchAPI to extract all users that have interacted with this IP (from SIEM). Also extract all the incidents related to the above IP
- Uses SearchAPI to get the number of incidents this user is associated in the last 12 hours
- Sends an email to the required address (completely customisable) with the list of those incidents info (this could be your SOC's email, or analyst's email) and waits for response
- Use IncidentAPI to mark this incident as resolved and Close the Case, when the email gets an response.
This playbook can be nested with other playbooks or you can run it independently. Please be aware that when you run it independently, it will create a case item.
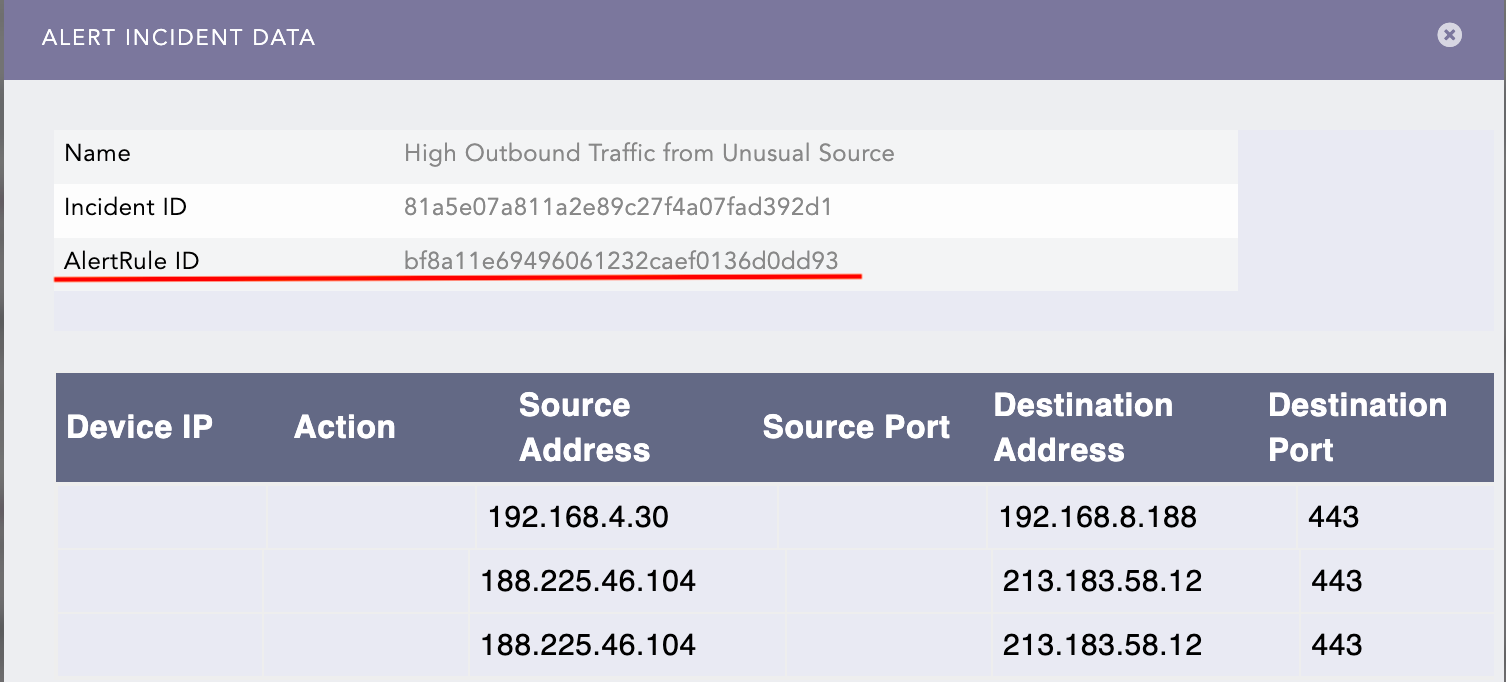
Do try and let me know what you think. Please feel free to modify and add other interesting workflows that can be automated, and share back.
Niklas
-
How to Extract Custom SAP Table Modification Logs in SIEM Using LogPoint for SAP?
Hello everyone,
I hope this post finds you well. Today, I'd like to discuss how to extract custom SAP table modification logs in SIEM using LogPoint.
For those unfamiliar with the concept, SIEM (Security Information and Event Management) is a technology that combines security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by network hardware and applications.
LogPoint is an industry-leading SIEM solution that enables users to collect and analyze log data from various sources, including SAP systems.
When it comes to SAP systems, LogPoint can be used to extract modification logs for standard tables. However, for custom tables, some additional configuration is required to ensure that the logs are collected and analyzed properly.
Here are the steps you can follow to extract custom SAP table modification logs in LogPoint:
Step 1: Enable Change Document Object
First, you need to enable the change document object for your custom table. You can do this by using the transaction code SCDO. Once you have enabled the change document object, SAP [ https://www.lenovo.com/ca/en/servers-storage/solutions/sap ] will start creating logs whenever a change is made to your custom table.
Step 2: Define Change Document Object for Logging
Next, you need to define the change document object for logging. You can do this by using the transaction code SCU3. In the Object Attributes tab, select "Change Documents" and then choose the "Create/Change" option to define the change document object.
Step 3: Define Logical System Name
Now, you need to define the logical system name for your SAP system. You can do this by using the transaction code SALE. In the "Logical Systems" option, select "Define Logical System" and then create a new logical system name.
Step 4: Configure the RFC Destination
Next, you need to configure the RFC destination. You can do this by using the transaction code SM59. In the "RFC Destinations" option, create a new RFC destination for your SAP system.
Step 5: Configure the Data Source in LogPoint
Finally, you need to configure the data source in LogPoint. To do this, go to the "Sources" tab in LogPoint and select "SAP" as the source type. Then, configure the data source by entering the RFC destination details and selecting the custom table for which you want to extract the modification logs.
In conclusion, extracting custom SAP table modification logs in SIEM using LogPoint requires some additional configuration steps. By following the steps outlined above, you can ensure that the logs are collected and analyzed properly, enabling you to detect and respond to potential security threats in your SAP system.
I hope you found this post helpful. If you have any questions or suggestions, please feel free to share them in the comments section below.
-
ChatGPT-SOAR integration now available for Logpoint
Hi All,
Have you tried our new ChatGPT-SOAR integration yet? The OpenAI Actions will allow you to ask ChatGPT anything and incorporate the responses into your playbooks and use cases. The actions require valid credentials you can apply for at platform.openai.com/signup. The actions allow you to send requests, receive answers and modify the model used for receiving results.
To read more about the use cases: https://www.logpoint.com/en/media-room/#/pressreleases/logpoint-makes-chatgpt-soar-integration-available-3232134
To download: https://servicedesk.logpoint.com/hc/en-us/articles/9183395790237-ChatGPT-Integration
-
Vendor rules sharing
Hey there,
I’m not available to comment on the post from a year ago and I have follow-up questions:
Mike Blomgren in his reply stated that in order to “share Alert Rules with User Groups, you need to Clone the Vendor Rule”. My questions are as follows:
- Does it work the same way with the “Vendor rules”? Is there an option to share the “Vendor rules”?
- If so, is there an available solution to share multiple (like 50 or more) vendor rules? Do you have to clone them all?
Thank you in advance.
-
Combining formatted messages from ForEach?
Hi folks,
I was just wondering if there was a way to combine formatted messages into one result from a ForEachResult loop?
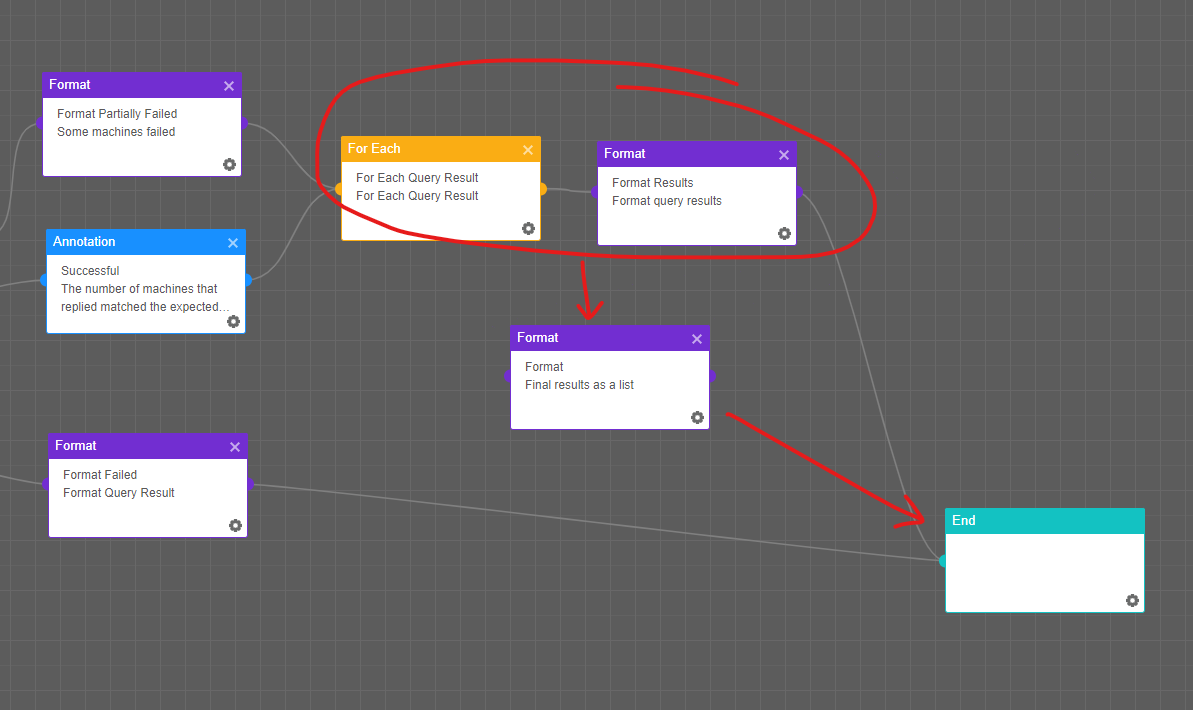
Diagram showing how I would like the results to combine. I currently have a little status message that is created by having the ForEachResult connected to a Format node. Unfortunately, I can’t think of a way to combine these created Format nodes into a single Format message that can then be used elsewhere.
I could feed the results into a Python script but that seems excessive for such a small thing (and would like to avoid if possible as it adds delay).
I also looked to see if I could have a ‘LIST’ global parameter, but that does not appear to be the case.
Any ideas?
-
What's the use case for 'Add Global Parameters' action in SOAR 1.0.4?
Hi folks,
I was wondering if anybody could tell me what the use case is for the new ‘Add Global Parameters’ action added in SOAR 1.0.4? As far as I can see, any output parameter from an action is already accessible from any other?
From my quick tests it doesn’t look like they pass down to Sub-playbooks either, so are they just meant as a quicker way to access the values within a playbook?
I couldn’t find any documentation on this, so I was hoping someone else might know the answer. -
Rename a case within a Playbook?
Hi folks,
Another cases and playbooks question - is there a way to update the name of an existing case item from within a Playbook?
By default, we are generating cases with just the incident ID for identification, but we’d ideally like to be able to update the name of the case once some additional playbooks have run.
We already have a way to get the case ID etc, it’s just the renaming part we’re stuck on.Is this possible?
-
Update case with output from Playbook
Hi folks,
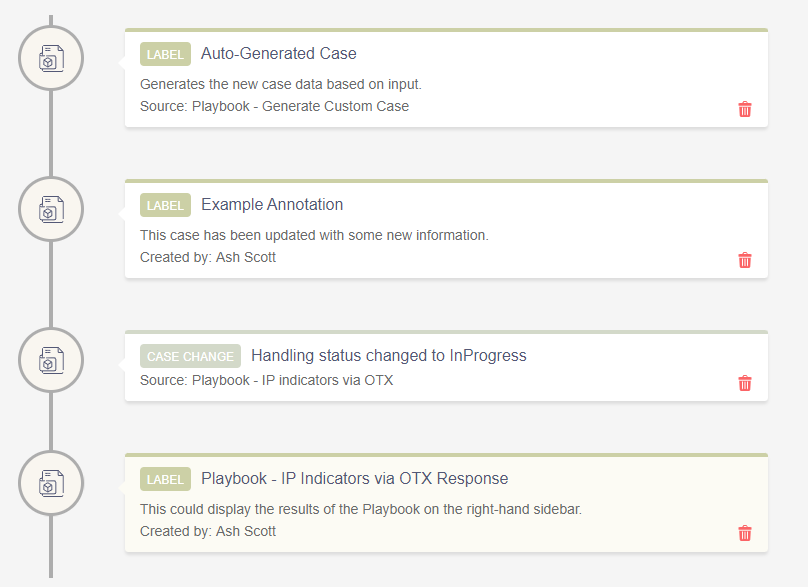
Is there a way to update a case with the output of a Playbook?
For example, if I have a Playbook that checks an IP Reputation, is there any way I can get the Playbook to update the case to display the reputation response as an actual Case Annotation or something of the sort?
-
Top 5 SOAR use cases
Analysts are constantly swamped with alerts, and to deal with this, they have to rely on repetitive manual tasks. This is like putting water on an oil fire, making the situation much worse and more time-consuming.
SOCs need a solution that enables them to manage and prioritize their workflow efficiently by giving them the ability to collect security threat data and alerts from multiple sources. This is where Logpoint steps in.
Previously we identified top use cases for SIEM . This time here are five common SOAR use cases that every organization should implement to reduce alert fatigue, overload and subsequently increase productivity in your SOC team.
01 Automated alert triage and enrichment
02 Endpoint malware mitigation
03 Automated Phishing Investigation and Response
04 Automated Threat Intelligence management
05 Ransomware mitigationTo read the full story, read the link below: https://www.logpoint.com/en/blog/top-5-soar-use-cases/
-
Introducing /logpoint Playbook Explorer
Hi All,
Have you ever found yourself asking the following questions while using /logpoint SOAR?
-
What do i need to do to run a specific playbook?
-
What playbooks can i run with my current set of integrations?
-
What integrations should I get to run a specific playbook?
In case the answer is yes, we have exciting news. We are pleased to announce the launch of /logpoint playbook explorer, a compact tool helping you to maximize the security value of your integrations and SOAR playbooks.
For your convenience, we have also created a short walk-through video attached below.
You can access /logpoint playbook explorer via the link below:
https://docs.logpoint.com/playbook-explorer
Should you have more questions, do not hesitate to reach out to us here or via customersuccess@logpoint.com
-
-
SOAR VirusTotal API integration
Hi, Is anyone using the VirusTotal integration into their SOAR?
I was all for getting it setup until I saw that you cannot use the free Public API in a commercial product.“The Public API must not be used in commercial products or services.” ( https://developers.virustotal.com/reference/public-vs-premium-api )
So, is anyone using the Premium API? and is it really $10,000 per year?
Or are you sticking to the public API and hoping to not get blacklisted?
Cheers
-
Top 5 SOAR Use Cases
Analysts are constantly swamped with alerts, and to deal with this, they have to rely on repetitive manual tasks. This is like putting water on an oil fire, making the situation much worse and more time-consuming.
SOCs need a solution that enables them to manage and prioritize their workflow efficiently by giving them the ability to collect security threat data and alerts from multiple sources. This is where Logpoint steps in.
Previously we identified top use cases for SIEM . This time here are five common SOAR use cases that every organization should implement to reduce alert fatigue, overload and subsequently increase productivity in your SOC team.
01 Automated alert triage and enrichment
02 Endpoint malware mitigation
03 Automated Phishing Investigation and Response
04 Automated Threat Intelligence management
05 Ransomware mitigation01 Automated alert triage and enrichment
Logpoint SOAR automates alert triage and enriches the alerts with additional information from multiple sources enabling analysts to focus on incidents requiring human intervention.
Usually, SOCs must deal with security alerts by manually reviewing and investigating all security alerts that lack additional context. That is a challenging and costly circumstance.
Logpoint SOAR integrates with many solutions, such as HR or travel systems. This functionality allows additional information to accompany the alert, which means the threat(s) are dealt with swiftly.

02 Endpoint malware mitigation
Endpoints are increasingly targeted by malware attacks, with smartphones and laptops being the most vulnerable targets. The occurrences are increasing due to the move to remote working and endpoints operating outside of the organizational network.
These circumstances generate false positives or low severity cases, and addressing these manually results in long response times, thus increasing risk.
Within seconds Logpoint SOAR can orchestrate and automate actions to investigate and respond to the high volume of alerts and determine the severity and respond accordingly, ensuring that the security team prioritizes the most critical malware attacks, drastically minimizing risk.

03 Automated Phishing Investigation and Response
Phishing attacks are not going anywhere soon, and in fact, they are on the rise. Did you know that 36% of data breaches involve phishing attacks?
Manually investigating a phishing alert can take hours or even days for the analysts and require multiple security tools.
Logpoint SOAR accelerates the phishing investigation and response time from hours to minutes with out-of-the-box and automated playbooks, which severely reduce time wastage and, in contrast, aid efficiency and productivity within SOC teams.

04 Automated Threat Intelligence management
Logpoint SOAR automatically collects and centralizes threat data from various threat intelligence sources, ensuring analysts can leverage the most current threat intelligence data and can use it to discover malicious indicators or to understand how different alerts are connected.
This enables faster response times to real threats and drastically minimizes risk.
Logpoint SOAR’s threat intelligence capabilities include the centralized collection of TI, a lower risk rating on a TI feed based on actual false positives found, and fusion and deduplication of TI feeds.

05 Ransomware mitigation
A considerable percentage of organizations were victimized by ransomware last year, and the attacks are on the rise, with variants constantly evolving.
Manual responses to these attacks are challenging as the techniques used are becoming more advanced, and more companies are willing to pay for their data to be recovered. Therefore, rather than constantly improving existing endpoint protection platforms, companies should use a solution that can successfully detect and respond to the attacks.
Here time is a critical factor. Logpoint SOAR acts quickly and automatically based on the classification of the alerts mapped to the MITRE ATT&CK framework. Detection, classification, investigation, and response are tied together, further expediting the incident investigation process.

For more in-depth information on these use cases check our SOAR brochure or ask for a demo via customersuccess@logpoint.com
-
Unable to receive the logs from 0365?
Using logpoint to fetch logs from Microsoft Office 365 but unable to receive the logs of emails (like:- email delivery etc ) except the mail delivery fail logs.
Able to fetch the logs like:
-Mail delivery failure
Not able to reveive the logs like:
-Mail delivered
Any suggestion? Any Solution?
-
Masterclass - Danmark recording
Tak til alle der deltog i vores seneste Masterclass for Norden. Glem ikke at gå ind og registrere dig til vores næste Masterclass d. 26 April, du kan læse mere her: https://go.logpoint.com/Nordic_Masterclass_2022. Hvis du ikke fik chancen til at se det live kan du her se optaglesen samt præsentationen.
-
We are excited to announce our newest global service: Playbook Design Service.
Our converged SIEM+SOAR performs automated investigation and response to cybersecurity incidents using playbooks. Playbook Design Service is an additional service assisting organizations with refining and optimizing your manual incident response processes into documented workflows and automated playbooks tailored for your organization. Our service encompasses a complete playbook lifecycle, from understanding your specific needs to the creation, development, and testing of the playbook. Having our Global Services experts by your side enables utilizing your SIEM to its fullest extent, reducing your workload, and increasing your ROI on security controls.
For more information, download our Playbook Design Service brochure: https://go.logpoint.com/playbook-design-service?_ga=2.39629923.1196326192.1645625385-1446914226.1645171249&_gac=1.261194623.1642752963.CjwKCAiA0KmPBhBqEiwAJqKK412rigizVIxknwM7T0qJ3YeUrzEpvCi5Q4a5OEID4NJS455Nz2QDixoCaZUQAvD_BwE
-
Live session introducing LogPoint SOAR
Hi All,
Just wanted to remind you of the awesome opportunity to join our live session with Doron Davidson, LogPoint VP Global Services, who will introduce LogPoint’s new capabilities to automate incident detection and response.
Join the session to:
- Learn how automatic response playbooks reduce the mean time to respond
- See a product demo of common use cases
- Understand the value of truly native response capabilities in LogPoint SIEM
Joining links:
Oct 5 for Partners: https://logpoint.zoom.us/webinar/register/WN_lSn4uIOsSPqlMrv03T4c1Q
Oct 7 for Customers: https://logpoint.zoom.us/webinar/register/WN_LwrLoaX5SgKLRF-A4l1Nsw
Oct 12 for Visitors: https://logpoint.zoom.us/webinar/register/WN_3Lf-tA0yTHKOa5cCyM1ATg