SIEM - Searching & Analytics
-
LogPoint alert bug where it doesn't use search filtering with ">" or "<" symbols
Hello,
Hope all is well,
I have encountered a bug within LogPoint alert rule queries were all default and custom alert rules that utilise symbols ">" or "<" to finalise alert logic fails to use these symbols and all other data that was added after those symbols. If you run the alert rule query by copy pasting it to the search manually, it works as it should, but if you want that query to be used by an alert (alert query) it drops everything that is beyond and including the symbols "<" or ">".
Example of this bug:
Multiple default LogPoint alerts utilise end of alert logic with filtering command similar to this "| search Event>10" but once the query is executed by the alert itself this filtering command is being cut and is executed as "| search Event" that produce incorrect results.This seams like a straight forward bug that LogPoint support should be aware of, is there a fix for it? any workarounds?
Appreciate the support,
-
Data Not Showing on AgentX Dashboard
Hi All,
Has anyone else experienced the same issue? I'm receiving AgentX logs, and everything seems to be working fine, but I can't see any data on the AgentX dashboard. I've also selected the correct repository.
-
Search for IP Range
Hi Everyone,
Was wondering if it's possible to search for an IP range among logs collected.
For example I might want to search for anything between 10.0.0.1 and 10.0.0.50 which would make investigations easier instead of searching for individual IP's.
Thanks in advance. -
distinct_count and followed by Issue while fetching Azure AD sign in logs
Office365 logs are sending duplicate events. So the generic usecase doesnt really work
[10 label=User label=Login label=Fail having same user] as s1 followed by [label=User label=Login label=Successful] as s2 on s1.user = s2.user
[col_type=office365 label=User label=Login label=Fail | chart distinct_count(id) as CNT by user | filter CNT>2] as s1 followed by [col_type=office365 label=User label=Login label=Successful] as s2 on s1.user = s2.user | chart count() by s2.log_ts,s2.user
Here "id" represents request id in azure AD, which is unique and thats what i want.
- Even if there isn't any output from s1, still I get some result from total query
- Also, i dont exactly get the followed by event, i get all success events in the timeframe
-
Search query for vulnerability score divided into three different levels.
HI,
We are using the Rapid7 fetcher and with the score field I want to make a widget where we divide these score into three different levels namely:
- Low with a score between 0 and 600.
- Medium with a score between 600 and 800.
- High with a score between 800 and 1000.
My issue is that I can't find the right search query to let me see this data the way I explained. I hope you may know the right query I need to use to get the result of the divide levels to work.
Thanks in advance.
-
File moved and File deleted
Hello Logpoint Community!
I’ve recently begun with the process of trying to create a search template to look up a user, and see recently moved files, or recently deleted files. I’m assuming this needs to be two seperate templates.
Anyhow, when browsing the file audit logs, I was baffled at the amount of logs generated by moving one file. In our environment, when moving one file, it generates upwards of 14 log entries, all with actions like “requested”, “access” - some log entries have the path of the file, some don’t.
Anyways, before I commit what I assume would be a long time trying to create this from scratch, I was wondering if some of you would be able to share a template to look up files moved by a user.In my mind it would look something like this.
| Timestamp | Username | File_path_old | File_path_new |
Any help at all would be appreciated!
Thanks in advance
-
Correlate target_id and target_user
Is there an easy way to correlate the target_id and target_user for Windows events that do not have a target_user value?
For example: what a user is added to a group, only the target_id is displayed in the event, but we also want to show the target_user in the event or dashboard. -
LogPoint pySigma Backend
Hi
Just to draw your attention to this new tool.
Though still in preliminary stage, certainly worth trying.
-
How to extract user from regex in search?
Hello folks,
I am attempting to extract data for users who have browsed torrents. I've applied a regex query to match users, but it's returning all users instead of only those matching the regex.
Here is a query : "user"=* application=bittorrent | process regex("^[a-zA-Z]\.[a-zA-Z]+\d*\.\d{2}$",user )
If anyone know what I am missing, love to hear.
Thanks
-
FileShare missing logs
Hi,
I need you help form an issue that I have about the FileShare logs. In fact, when a user download the files form fileShare I didn’t have any log to shows downloaded file. In fact I receiving juste the “ sycnhronisation ” logs :
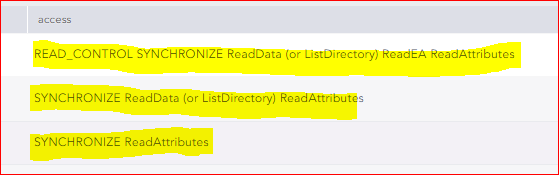
Could you please tell me how can I do to receive the logs from fileshare to show when a user download or copy file ?
Thank you in advance for your help :)
Regards,
Siawash
-
Data privacy on dashboards
I have activated the “Data Privacy” module and configured the fields, concerned groups, etc.
I have a dashboard whose query contains one of the “encrypted” fields defined into “data privacy” module. Since activation, the dashboard is not displaying information anymore.
There is a way to allow (via request/grant or something else) the dashboard to display the information ?
Thanks,
Alexandru -
Performance Question: Has the order of search parameters influence on search performance?
Hi everyone!
does anyone know if it makes any difference how you order the search parameters in a search query?
example:
event_id=1234 event_channel="Security"vs.
event_channel="Security" event_id=1234 -
several if-else
Hi everyone, i have a issue:
I am writing a query. My query contains more than one if-else. However, because there are too many if-else, it does not return any result and gets stuck in “searching”. I wonder if there is a limit for else-if? If there is a small amount of else-if, it works, the query works, but if there is too much, unfortunately it doesn't work. I need help with this!!! since the values corresponding to each condition are different, I should use the else-if structure. I am open to different solution methods by the way.
The query I wrote is as follows (here I just wanted to draw attention to the amount of else-if)
I also get the following error: “No Response from server”alert=*
| process eval("
foo=if(alert=='xyz1') {return 1.2}
else-if(alert=='xyz2') {return 1.0}
else-if(alert=='xyz3') {return 1.21}
else-if(alert=='xyz4') {return 1.2}
else-if(alert=='xyz5') {return 1.29}
else-if(alert=='xyz6') {return 1.25}
else-if(alert=='xyz7') {return 1.29}
else-if(alert=='xyz8') {return 1.200}
else-if(alert=='xyz9') {return 1.24}
else-if(alert=='xyz10') {return 1.25}
else-if(alert=='xyz11') {return 2.2}
else-if(alert=='xyz12') {return 0.2}
else-if(alert=='xyz13') {return 13.2}
else-if(alert=='xyz14') {return 1.2}
else-if(alert=='xyz15') {return 5.2}
else-if(alert=='xyz16') {return 9.2}
else-if(alert=='xyz16') {return 55.2}
else-if(alert=='xyz17') {return 9.2}
else-if(alert=='xyz18') {return 6.2}
else-if(alert=='xyz19') {return 10.2}
else-if(alert=='xyz20') {return 18.2}
else-if(alert=='xyz21') {return 19.2}
else-if(alert=='xyz22') {return 9.2}
else-if(alert=='xyz23') {return 71.2}
else-if(alert=='xyz24') {return 19.2}
else-if(alert=='xyz25') {return 16.2}
else-if(alert=='xyz26') {return 9.2}
else-if(alert=='xyz27') {return 41.2}
else-if(alert=='xyz28') {return 18.2}
else-if(alert=='xyz29') {return 19.2}
else-if(alert=='xyz30') {return 121.2}
else-if(alert=='xyz31') {return 1.221}
else-if(alert=='xyz32') {return 11.2}
else-if(alert=='xyz33') {return 156.2}
else-if(alert=='xyz34') {return 15.2}
else-if(alert=='xyz35') {return 12.2}
else-if(alert=='xyz36') {return 1.2}
else-if(alert=='xyz37') {return 1.2}
else-if(alert=='xyz38') {return 15.2}
else-if(alert=='xyz39') {return 1.2}
else-if(alert=='xyz40') {return 15.2}
else-if(alert=='xyz41') {return 16.2}
else-if(alert=='xyz42') {return 19.2}
" )| timechart count(alert) as cnt by alert, foo every 1 day
| timechart sum(foo*cnt) as t1, sum(cnt) as num every 1 day
| timechart sum(t1/num) as risk every 1 day -
Report
When I try to create a report it says “”Invalid number of fields used in process command, expected 7 field(s) but found 8” Why?
-
Alerts repetation
Hi,
I would like to know if is it possible to receive one alert for the same action? For, example : for the following example if the same action is repeated several times I want to recive just one alert not more.
action=Login source_address=1.1.1.1 user=titi | chart count() by user
Is it possible ? If yes could you please tell me how do I do ?
Best regards,
SA
-
Usage of computed fields into process functions
The following query put the result of processing function as “null” :
| chart max(log_ts) as maxlogts | process format_date(maxlogts,'YYYY/MM/dd') as endDate | fields maxlogts, endDate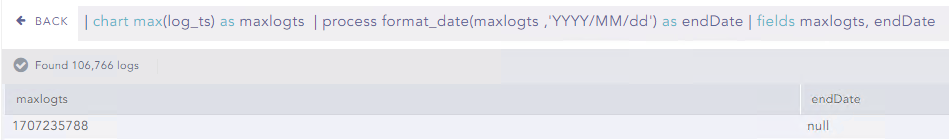
I think the field “maxlogts” is not retrieved/recognized by function format_date().
There is a way to obtain the field “endDate” not null ?
-
use Joinner method in Templates
Hi,
I Would like to use the joinner method in my template LogPoint. Whowever, I can’t use the “{{}}” for search parameter. Could you please tell me how should I do ?
Here is an exemple of this tamplate :
[ source_address=* display_name=* user=*] as s1 join [ user=* source_host=* source_address=* ] as s2 on s1.user = s2.user {{source_host}} | rename s2.source_host as source_host | process geoip(s1.source_address) as country| rename user as User | chart count() by User, country, source_host
Note => I would like to search by this parameter {{source_host}}
Thank you in advance.
Siawash,
-
Prefered Way to Fetch Logs from Azure?
Hi,
what is LogPoint's recommended way to get logs from Azure AD / EntraID and any other Azure applications into LogPoint?
We have noticed that the Azure EventHubs sometimes provide their logs several days late via the message queue. We were able to verify this independently of LogPoint using a fetcher developed in Python.
How does this work with the " Azure Log Analytics Workspace" module? Can the logs be expected in the SIEM in a timely manner?
A delay of several hours and days is not possible with the current alert rule concept of searching on already indexed timeranges without running the alert rules on utopian high timeranges.
-
Filter only part of a field
Hello
We want to see a statistic of outgoing mails/which domain sends how many.
Filtering by source user is easy, however what I would need is the domain, not the precise E-Mail address.
Is there a way to filter by only what comes after the @, so I can make a chart with only that information.
Or is there a way to get the more precise Domain.
cheers, and happy holidays
Mike -
Usage of process eval like
Hi guys,
I wrote a query that monitors for abnormal computer names joining my organization network. I had some success with those queries, but they still returns some false positives for me. How can I improve it?
| process eval("is_abnormal_computer_name = (machine != like('Computer_Name') AND machine != like('Computer_Name') AND machine != like('Computer_Name') AND machine != like('Computer_Name'))")| process eval("is_abnormal_computer_name != like(machine, '^(name|name|name|name).*')")I want the query to returns the computer names that are abnormal.
-
Publish Dashboard to Public API
Hello all,
I am looking for a way to publish a dashboard to the public API. Does anyone know if this is possible?
As it stands I have managed to publish individual dashboard widgets to the public API but I would prefer to share the whole dashboard with 1 URL.
Thanks
-
list all event ids found by each device
I need to create a query to export the results with the following criteria, but unsure how to write the query.
I want to list every end device by hostname (including all end devices fed by Windows event collectors, not reported as the WEC) and then all the event codes (unique) collected from that device in ascending order.
Can someone please point me in the right direction
-
Exiration log for Microsoft office 365
Hi,
I would like to know if it is possible to find the log that show the expiration date of Microsoft office 365 account ? If yes, could you please tell me how can I find it ?
Regards,
Siawash
-
Logpoint Agent X Applocker Dashboard
Hi.
We have implemented Agent X into our systems, and we are observing Applocker Events with Agent X.
Now our customer would like a dashboard for these Event.
And I was not sure how to go about creating these Dashboards.
How can I make a dashboard specifically for the Eventviewer logs.
Cheers Mike -
P2P network connection detect rule
Hello everyone,
Being searching LP blogs and community to see if we have any detection rules for P2P network connections. Came out there is a rule to finding P2P applications but nothing of useful to find the network connection. Any tips or suggestions in building a P2P detection will be much appreciated.Thanks
-
Add subnets to list
Hi, how can I paste a list of subnets to a static list?
I'm trying to add a list of subnets to a static list in Logpoint (7.3.2). e.g.:
1.2.3.0/24
2.3.4.0/24
5.6.7.0/23
4.3.2.0/22
I cannot just copy/paste the list as it is pasted as one entry. -
Access individual logs within single stream
Hi,
I want to display all relevant information that is available for remote sessions per remote session. However this is contained in different logs that all have the same session_id. Suppose I gather those logs in a search via a single stream. For example like this:
[3 user=”x*” type=login OR type=logoff OR type=authentication_try having same session_id] as StreamHow can I access the individual logs included?
For example
| fields Stream.type, Stream.col_ts, Stream.user or
| chart count() by Stream.user etc. doesn’t work.
Just showing the fields without grouping of same session_id is not the solution, since I cannot order fields and all session_ids are mixed.
Hope there’s a way. Best
Georg -
group logs with same value
Hi everyone,
Here is a task that puzzles me: I am looking at events of remote connections and I want to display the connections that are currently active. One Connection has evetns like “login”, “authentication_try”, “session_closed”, etc. and the same session_id. The number of logs with the same session _id may vary, since, for example, there might be more than one authentication_try.
So I would like to first group all events with the same session_id and then filter out those, that do not have a “session_closed” event.
I tried to implement this with one or two streams (join) but did not come to a solution. With one stream I cannot give an exact number of logs “having same session_id”, with two streams I would need something like
“[session_id=*] as first-stream
join[session_id=*] as second-stream
on first-stream.session_id=second-stream.session_id AND first-stream.log_ts!=second-stream.log_ts”. Also a “not followed by” could have been a solution for this, which does not exist.
Does anyone have an Idea how to accomplish this (without using a Playbook).
Best regards
Georg -
Dynamic Alert Recipient
Hi all,
i would like to send an email alert and choose the recipient depending on the triggered alert. For example, when a user changed his active directory password, i want to send him an email, telling that the password for his account was changed and if it was not himself he should contact directly the helpdesk.
Best
edgar
-
Logpoint Agent X and devices Hostnames
Hello
with the new Agent X, we were testing adding Devices with Agent X to logpoint, due to DHCP they will not always have the same IP address. We attempted to add this device via Hostname to logpoint, but even though the Agent X panel claims that it is active and collecting logs, When searching for said logs, I get no result for the Hostname.
Is it Possible to use Hostnames to add Devices to logpoint in use with agent X?
Or is it not possible.