SIEM - Use Cases
-
search current hash into logpoint without adding or connecting with threat feeds
we need to search hash in logpoint of our current endpoint and servers. how we can do that. is there any package we need to install for particular application or anything else.
-
Enable FIM in Logpoint
I want to implement FIM use cases in logpoint. please share any document or implementation guide to achieve the below.
-
How to estimate the volume of data collected ?
Hello,
I would like to search a query to know the volume of data per day collected in my Logpoint.
Thanks a lot
-
Collect DHCP logs & enrichment with other log sources
I’m thinking of onboarding internal DHCP logs. But I don’t quit know yet If it’s a good way to go.
I’m also in the progress of onboarding ISE logs, for authentication monitorering. Is It possible to correlate DHCP logs with ISE logs?
How about use-case related to DHCP logs? Looking at the built in alert rules there was only few use-cases related to DHCP.
I think more about rouge DHCP server and so on.
Does anyone have experience about DHCP logs and the the ability to correlate these with other logsources to get MAX out of It.
Thanks! -
Integration with Salesforce Commerce Cloud
Does Logpoint has out of the box integration with Salesforce Commerce Cloud? Has anyone did this from this group? Appreciate if you could help!
-
Help-Query for user logged into multiple systems
Hi,
I am looking for a query for finding ‘users logged into multiple machines’. Can someone please help me out.
Thanks in Advance,
KP
-
Cisco Stealthwatch send syslog to LogPoint
Hi!
I’m wondering If It’s possible to configure Stealthwatch to communicate with LogPoint. I want Stealthwatch to forward events, even better If It also can forward flows to the SIEM.
Is this possbile?
All I can find regarding this is the integration with LogPoints SOAR to configure different types of actions.
Adding the Vendors — Cisco Secure Network Analytics (Stealthwatch) SOAR Integration latest documentation (logpoint.com) -
Emerging Threats: AgentTesla – A Review and Detection Strategies
AgentTesla [ S0331 ] a.k.a Negasteal is a
.NET-based Remote Administrator Tool (RAT) first detected in 2014. It is advertised as a Remote Administrator Tool since then. AgentTesla allows adversaries to remotely control the systems of victims and manipulate them accordingly, so it is utilized by numerous threat actors such as SILVERTERRIER , SWEED , Aggah , and many more.Learn more about the analysis, detection, and mitigation using Logpoint SIEM+SOAR in our latest report on the link below.
https://www.logpoint.com/en/blog/agentteslas-capabilities-review-detection-strategies/
-
Webinar: Introducing Agent-X
Hi All,
We are excited to introduce AgentX , as a key native element of our Converged SIEM platform.
AgentX greatly helps to elevate threat detection, accelerate investigation, and ensures lightning-fast remediation while working seamlessly with SIEM and SOAR .
If you would like to hear more, join our upcoming webinar via the link below.
https://www.logpoint.com/en/webinars/agentx-webinar-endpoint-security/
-
Gamaredon and their new “Gamma“ edition of malware TTPS
A year on since the first attack on Ukrainian territory and the unofficial beginning of the cyber war, the Secretary of Ukraine’s National Security and Defense Council, Oleksiy Danilov , has issued a warning that Russia could conduct a large-scale cyberattack as part of its renewed aggression. Through this updated edition of the Russia-Ukraine war, we look deeper into its execution, techniques they have deployed, the variations, and how we can utilize the capabilities of Logpoint Converged SIEM to detect, prevent and respond to attacks from Gamaredon and their new “Gamma“ edition of malware TTPS.
-
Utilizing Network Logs for Investigation and Remediation to uncover illegitimate Crypto-Mining Activity (Cryptojacking)
Crypto-mining has become a growing threat in recent years with more than 500,000 individuals affected only in 2022 according to Kaspersky reports. Typically using processing power of the victim’s computer illicitly to mine cryptocurrency, allowing cybercriminals to remain hidden for months.
In our newest piece by Logpoint blackbelt , Swachchhanda Shrawan Poudel you can read about the best practices and tips&tricks to detect and remediate illegitimate Crypto-Mining Activity with Logpoint.
Read the full article on the link below:
https://www.logpoint.com/en/blog/uncovering-illegitimate-crypto-mining-activity/
-
Why this error message ? '}'
Hi,
I come to you because I have an error when I execute folloing query. Could any one help me please ?
Here is my quary :
(MsWinEventLog OR norm_id=WinServer*) label=Object label=Access (access_list=\"*4417*\" OR access=\"*WriteData*\") {{user},}, {{fileshare},}, {{path},}, -relative_target in SYSTEM_PATHS | rename relative_target as Object, share_path as Path | chart count() by user, device_name, object_type,Path, Object | fields user, device_name, object_type, Path, Object
and when I execute this query I receive these error message :

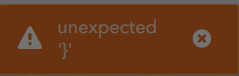
Thanks in advance
Looking forward to reading you -
Adding a Search Template
Hi,
I would like to add a new parameters templete. But when I add the new parameter it doesn't works (for exemple when I add the source_address it doesn't works) ? I would like to know why ?
Thank you in advance for your help.
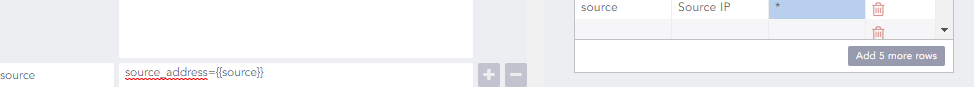
-
How to create a case from incident with in-built soar?
I have a requirement of creating cases from incident tabs. Can i get a reference to creating cases from incidents?
-
Firewall Use Cases V1.0
Hi All,
In this second instalment of the Use Case catalogue series, we are focusing on Firewalls. Firewalls are a vital part of most organisations and enterprises today. In this Use case catalog you will find a collection of analytics available for firewalls in Logpoint SIEM for PaloAlto, Cisco, Fortinet and Check Point firewalls.
-
Hunting LockBit Variations using Logpoint
LockBit has been implicated as the most active ransomware and has been involved in the most attacks compared to others of its kind. Read our latest blog by Anish Bogati & Nilaa Maharjan from Logpoint Global Services & Security Research on how Logpoint can help you to strengthen your security posture when it comes to LockBit ransomware.
Link to the blog post:
https://www.logpoint.com/en/blog/hunting-lockbit-variations-using-logpoint/
-
Introducing the Logpoint Use Case Catalog
Focusing on one use case at a time, the Use Case Catalogue will guide you through the implementation of basic monitoring of specific log sources in a Logpoint SIEM platform. The first instalment of the Use Cases Catalog series, Active Directory Use Cases is now available on the link below: https://community.logpoint.com/active-directory-13
-
Passing parameters within a Playbook Trigger?
Hi folks, I’m trying to set up a Playbook Trigger, but wanted to potentially pass through parameters for it.
The setup is as follows:
- Alert is triggered
- Playbook Trigger runs based on matching alert_id
- Playbook generates case data and runs additional actions/playbooks.
I would (ideally) like the Playbook Trigger to pass details from the incident to the Playbook it is linked to.
Is this something that’s possible from the Trigger directly, or do I need to use a Query/another action within the Playbook to try and extract the info I need?
On that note, is there an easy way to get data from the incident that triggered the alert within the playbook itself?
-
Emerging Threats: ChromeLoader
Our research team have been taking an in depth look at ChromeLoader. An innocent looking malvertiser that masquerades as a cracked game or a pirated movie sometimes placed on social media.
Read here ⇉ https://bit.ly/3N2vHEo and download the report here ⇉ https://bit.ly/3tRZZDc to ensure you’re taking the best steps to remain protected.
#SIEM #SIEMSOAR #Cyberthreats #CyberSecurity #Malware -
Spring has finally sprung! But this #Bumblebee isn’t interested in pollination - This one’s a malicious downloader.
In the third instalment of our Emerging Threats series our researchers took a look at Bumblebee’s evolution and determined how you can best protect your organisation with in-depth analysis and response via #Logpoint
For the full article, click here: https://www.logpoint.com/en/blog/buzz-of-the-bumblebee-a-new-malicious-loader/
-
BoxAudit_v5.1.1 application release
We have released the BoxAudit_v5.1.1 application publicly in the Help Centre.
To find out more, you can find the application package here: https://servicedesk.logpoint.com/hc/en-us/articles/360002071597 and the documentation here: https://docs.logpoint.com/docs/boxaudit/en/latest/
-
Fetshing Logs from Oracle DB on Redhat
Hello everyone,
I want to collect oracle DB logs in redhat with SCP fetsher. does anyone know the exact locations of the logs.
NB: I have already tried with the logs of redo*.logs, but they are not readable.
Regards
-
LogPoint 6.12 - Speed up incident response with more contextual awareness
Join Sales Engineer @Nils Krumey on October 5 on a live session where he will demo how the new update to LogPoint can help security analysts react to and resolve threats quickly by knowing instantly which type of threat it is.
Join the knowledge session to:
- Learn how the new categorisation of alerts and incidents to the MITRE framework can speed up incident response
- See how you now can share search and report templates
- Understand how LogPoint is making it easy to route incidents to different SOAR playbooks based on the incident type
Register on the link below:
https://lnkd.in/ggg9pvMH -
Alarm a missing Event...
Hi @all,
do anyone have an Idea how to alarm a missing Event like:
Every Morning around 4 there should be a “successful copy” Event. I want to Alarm if exactly this Event is missing.
The Alarm should fire around 6 and not much later.
My only Idea is to run a scheduled Report because i can’t configure the ALarm to rum exactly in the Timeframe of 2 hours.
Am i wrong?
-
Fetching logs using Nessus Fetcher
Installed Nessus. Configured Nessus fetcher in LogPoint and communicated with Nessus successfully. What is the following procedure that the Nessus logs are imported to LogPoint?
Thanks in advance.
-
Has anyone been able to integrate TheHive for managing cases ?
I am trying to create a use case where i can connect TheHive with LP. Lets discuss if anyone has been able to or planning to do this
-
New Blogpost - Detecting PetitPotam
Remember to read the latest Blogpost
Watch out for PetitPotam, a relay attack that can compromise your domain without any authentication. In this blog post, our Security Analytics Engineer Babesh Rai takes you through all you need to know to mitigate the threat and detect the attack chain in LogPoint
Read the post here: https://www.logpoint.com/en/blog/detecting-petitpotam-a-relay-attack-that-can-compromise-your-domain-without-any-authentication/
/ Brian
-
Rules for monitoring attacks against web apps
Hi all,
I’ve been through the provided vendor rules in Logpoint and they are not useful. Does anyone have any rules that they can share that detect the attacks mentioned in the OWASP top 10?
Thank you
-
Fetching logs from Oracle Database table
Can we fetch logs from oracle database, where there is no incremental key? I am thinking about, fetching logs from database table on daily basis once.
Can it be possible with logpoint?