Welcome to Logpoint Community
Connect, share insights, ask questions, and discuss all things about Logpoint products with fellow users.
-
Performance Question: Has the order of search parameters influence on search performance?
Hi everyone!
does anyone know if it makes any difference how you order the search parameters in a search query?
example:
event_id=1234 event_channel="Security"vs.
event_channel="Security" event_id=1234 -
How to configure AbuseIPDB instance in LogPoint SOAR
Hi everyone,
I need to check some source addresses in my playbooks and I want to use AbuseIPDB for this action, but I can’t finish configuring AbuseIPDB instance and obtain some errors. Could you help me with the correct configuration for this instance in SOAR LogPoint Playbook integrations?. I have my api_key but I don’t know what is the correct base_url and threshold parameters if I need to review IP address.
I hope your help
Regards
Gabriel
-
how to configure AbuseIPDB instance
Hi everyone,
I need your help. I need to check Public IP Address in my playbook to obtain some information about it. I want to use AbuseIPDB but I’m obtaining error.
Bad/missing Action inputs! Details: Bad rest-action url: base url/check
I think the error is in my AbuseIPDB’s instance configuration. What is the base_url and threshold that I have to configure? I have my API Key ready.
Thanks for your help.
Regards,
Gabriel
-
When you comment a members reply there can go weeks before admin let your responce true.
Why is your admin’s so slow to approve answers, this is verry bad for people asking about a topic, they lose interest when it seems like no answers or suggestions are given.
I have now several times waited for weeks to see my suggestions get through. This should be instant, or you should remove the approve process !!!
Best regards Kai
-
Normalisation for Miliseconds
<123>2024-01-11T11:11:11.123Z hostname
I want to remove two fields from the above rohdaten using normalization, so to say. After normalization I should have the following fields:
milliseconds=123
log_ts=2024-01-11T11:11:11ZCan I do this in normalization (or signature)? If yes, can you write me the normalization/signature rule?
This problem can be solved like this:
| <<:int>><log_ts:datetime_m> <host:all>
but I don't want that. I want to separate my fields at the beginning using normalization.
-
several if-else
Hi everyone, i have a issue:
I am writing a query. My query contains more than one if-else. However, because there are too many if-else, it does not return any result and gets stuck in “searching”. I wonder if there is a limit for else-if? If there is a small amount of else-if, it works, the query works, but if there is too much, unfortunately it doesn't work. I need help with this!!! since the values corresponding to each condition are different, I should use the else-if structure. I am open to different solution methods by the way.
The query I wrote is as follows (here I just wanted to draw attention to the amount of else-if)
I also get the following error: “No Response from server”alert=*
| process eval("
foo=if(alert=='xyz1') {return 1.2}
else-if(alert=='xyz2') {return 1.0}
else-if(alert=='xyz3') {return 1.21}
else-if(alert=='xyz4') {return 1.2}
else-if(alert=='xyz5') {return 1.29}
else-if(alert=='xyz6') {return 1.25}
else-if(alert=='xyz7') {return 1.29}
else-if(alert=='xyz8') {return 1.200}
else-if(alert=='xyz9') {return 1.24}
else-if(alert=='xyz10') {return 1.25}
else-if(alert=='xyz11') {return 2.2}
else-if(alert=='xyz12') {return 0.2}
else-if(alert=='xyz13') {return 13.2}
else-if(alert=='xyz14') {return 1.2}
else-if(alert=='xyz15') {return 5.2}
else-if(alert=='xyz16') {return 9.2}
else-if(alert=='xyz16') {return 55.2}
else-if(alert=='xyz17') {return 9.2}
else-if(alert=='xyz18') {return 6.2}
else-if(alert=='xyz19') {return 10.2}
else-if(alert=='xyz20') {return 18.2}
else-if(alert=='xyz21') {return 19.2}
else-if(alert=='xyz22') {return 9.2}
else-if(alert=='xyz23') {return 71.2}
else-if(alert=='xyz24') {return 19.2}
else-if(alert=='xyz25') {return 16.2}
else-if(alert=='xyz26') {return 9.2}
else-if(alert=='xyz27') {return 41.2}
else-if(alert=='xyz28') {return 18.2}
else-if(alert=='xyz29') {return 19.2}
else-if(alert=='xyz30') {return 121.2}
else-if(alert=='xyz31') {return 1.221}
else-if(alert=='xyz32') {return 11.2}
else-if(alert=='xyz33') {return 156.2}
else-if(alert=='xyz34') {return 15.2}
else-if(alert=='xyz35') {return 12.2}
else-if(alert=='xyz36') {return 1.2}
else-if(alert=='xyz37') {return 1.2}
else-if(alert=='xyz38') {return 15.2}
else-if(alert=='xyz39') {return 1.2}
else-if(alert=='xyz40') {return 15.2}
else-if(alert=='xyz41') {return 16.2}
else-if(alert=='xyz42') {return 19.2}
" )| timechart count(alert) as cnt by alert, foo every 1 day
| timechart sum(foo*cnt) as t1, sum(cnt) as num every 1 day
| timechart sum(t1/num) as risk every 1 day -
Windows Server DNS Query Log
Hi all,
I have configured my windows 2022 dns server to log dns queries. We need those logs for security and possible forensic reasons.
The configuration is done in Windows Event Manager as described in DNS Logging and Diagnostics | Microsoft Learn . We are using LPAgent to collect other logs from this server.
The result is an etl file, which cannot be read from the eventlog with im_msvistalog configuration from LPAgent. etl cannot be read with the im_msvistalog plugin of LPAgent.
I have read that there is an NXLOG EE plugin im_etw out there which should be able to handle this file type, but we do not have the NXLog Enterprise Subscription.
Is there any other option to collect the dns query logs from the server and import them into LogPoint?
Is ther e any the best practice to handle windows dns server query logs (without using NXLOG EE)?
Kind regards
Uwe -
How to beat/win the splunk?
Hello, this is Yoshihiro.
I want to expand/sell Logpoint here in Japan.
But the splunk is very strong competitor here.
So I want to know any idea to sell/expand the Logpoint.
Like what is the strong point compared with it ?
Or If you were sales person kindly tell me about your experience when you won.
I got the answer about the license model in another portal like below.
~
You can beat the splunk easily by comparing the device-based Logpoint licencing/pricing to the splunk traffic-based licencing/pricing. A Splunk customer has to adjust its cost calculation when log traffic increases: https://docs.splunk.com/Documentation/Splunk/9.2.0/Admin/Aboutlicenseviolations#What_happens_during_a_license_violation.3F
~
I appreciated with him and I agree with it.
But honestly I need more idea about the function advantage.
For example I am not sure that the BCS for SAP would be important advantage.
Any idea?
regards,
Yoshihiro
-
How can I recover the pool configuration password?
Is there a way to get or change the configuration password for a Pool?
-
Report
When I try to create a report it says “”Invalid number of fields used in process command, expected 7 field(s) but found 8” Why?
-
Director Won´t let me Delete Device
Good Day Everyone
When trying to delete a device asset I get hit with this error “ Random hostname (Not the host name of the device I am trying to delete) does not appear to be an IPv4 or IPv6 network “
And it won´t let me delete the device,
I am not sure what to do about this, help would be greatly appreciated.
-
Alerts repetation
Hi,
I would like to know if is it possible to receive one alert for the same action? For, example : for the following example if the same action is repeated several times I want to recive just one alert not more.
action=Login source_address=1.1.1.1 user=titi | chart count() by user
Is it possible ? If yes could you please tell me how do I do ?
Best regards,
SA
-
Usage of computed fields into process functions
The following query put the result of processing function as “null” :
| chart max(log_ts) as maxlogts | process format_date(maxlogts,'YYYY/MM/dd') as endDate | fields maxlogts, endDate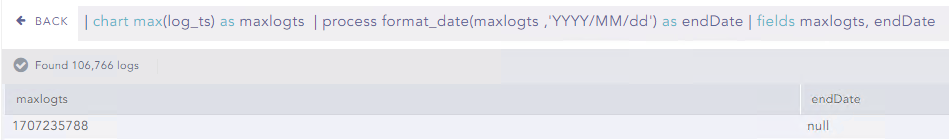
I think the field “maxlogts” is not retrieved/recognized by function format_date().
There is a way to obtain the field “endDate” not null ?
-
Logpoint 7.3.0 upgrade stalled
I have uploaded the logpoint 7.3.0 and 7.3.1 pak on logpoint server 7.2.4.
I have started the 7.3.0 pak installation but after some hours is still in “installing” state
Checking the status I see that is blocked on SOAR Plugin upgrade
………
…………...
Checking package status ...
install; giving etc/, storage/ and var/ to loginspect only in changed files
install; removing old files
install; copying files
Update; updating plugins....
Upgrading SOAR pluginI tried to install the 7.3.1 pak that fails because the 7.3.0 is not installed.
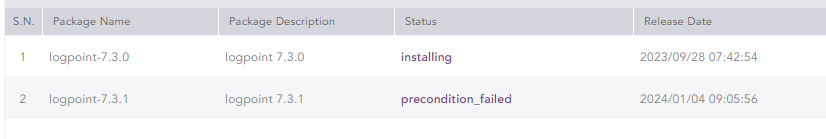
I have restarted the server but nothing change.
Could you please help me to understand the cause?
-
use Joinner method in Templates
Hi,
I Would like to use the joinner method in my template LogPoint. Whowever, I can’t use the “{{}}” for search parameter. Could you please tell me how should I do ?
Here is an exemple of this tamplate :
[ source_address=* display_name=* user=*] as s1 join [ user=* source_host=* source_address=* ] as s2 on s1.user = s2.user {{source_host}} | rename s2.source_host as source_host | process geoip(s1.source_address) as country| rename user as User | chart count() by User, country, source_host
Note => I would like to search by this parameter {{source_host}}
Thank you in advance.
Siawash,
-
WIndows Logs
We would like to send log files from a directory such as C:\Logs to our logpoint server.
What needs to be entered in nxlog.conf? -
Insidious Nightmares: Automating Employee Onboarding and Off-boarding
🔐 Goodbyes can harbor unforeseen risks, especially when departing employees possess crucial access and knowledge. Meet the "Lord Darths" of the corporate world—ex-employees with potent technical admin privileges, driven by motives to harm or exploit. Insider threats are real, and their impact can be substantial.
Consider the alarming history of insider threat cases; these individuals, armed with expertise and access, pose a considerable risk. Managing the employee lifecycle is pivotal and include everything from onboarding, retention, development, recognition, and exit. Our latest blog uncovers the critical stages of onboarding and exit - Check out the blog by Logpoint Security Analyst, Roshan Bhandari, on our website here or read key insights below:
Insights into Insider Threats
-
Staggeringly, 74% of respondents to a survey feel moderate to extremely vulnerable to insider threats.
-
The most critical impacts of insider attacks were loss of critical data ( 45% ), brand damage ( 43% ), and operational disruption or outage ( 41% )
-
Insider threats can be costly, 59% of the insider threat motivation was monetary gains while 50% was reputation damage .
-
The time to contain an insider threat incident increased from 77 days to 85 days , leading organizations to spend the most on containment .
Notable Insider Threat Incidents
-
The FBI arrests 21-year-old Air Force guardsman in Pentagon leak case.
-
A Yahoo lawsuit alleged an employee stole trade secrets upon receiving a Trade Desk job offer.
-
Proofpoint alleged an ex-exec took trade secrets to abnormal security .
-
A fired healthcare exec stalls critical PPE shipment for months .
-
An Apple lawsuit says 'stealth' startup Rivos poached engineers to steal secrets .
-
-
Prefered Way to Fetch Logs from Azure?
Hi,
what is LogPoint's recommended way to get logs from Azure AD / EntraID and any other Azure applications into LogPoint?
We have noticed that the Azure EventHubs sometimes provide their logs several days late via the message queue. We were able to verify this independently of LogPoint using a fetcher developed in Python.
How does this work with the " Azure Log Analytics Workspace" module? Can the logs be expected in the SIEM in a timely manner?
A delay of several hours and days is not possible with the current alert rule concept of searching on already indexed timeranges without running the alert rules on utopian high timeranges.
-
Filter only part of a field
Hello
We want to see a statistic of outgoing mails/which domain sends how many.
Filtering by source user is easy, however what I would need is the domain, not the precise E-Mail address.
Is there a way to filter by only what comes after the @, so I can make a chart with only that information.
Or is there a way to get the more precise Domain.
cheers, and happy holidays
Mike -
Usage of process eval like
Hi guys,
I wrote a query that monitors for abnormal computer names joining my organization network. I had some success with those queries, but they still returns some false positives for me. How can I improve it?
| process eval("is_abnormal_computer_name = (machine != like('Computer_Name') AND machine != like('Computer_Name') AND machine != like('Computer_Name') AND machine != like('Computer_Name'))")| process eval("is_abnormal_computer_name != like(machine, '^(name|name|name|name).*')")I want the query to returns the computer names that are abnormal.
-
Enable FIM in Logpoint
I want to implement FIM use cases in logpoint. please share any document or implementation guide to achieve the below.
-
Newbie: Distributed Logpoint
hello guys, good day
newbie here and I am taking overed from our previous employee. correct me if I’m wrong since it is still in final design
I need to deploy distributed LP in customer environment, we provide them 2 ESXi and this is our 1st customer migrated from Microfocus. The components are: (current)
- search head x1
- distributed logpoint x1
- log collector x2 (collect log for on-prem x1, collect log for cloud but sitting on prem)
for windows, planning to use LPA and the rest syslog
Issue 1:
I do some testing and I realized all the API or Cloud Trail configuration directly into DLP. Reason I am thinking, we do not need the LC on this case and the pros is we have the opportunity to turn on SOAR features also increase the specification/storage for DLP.
Do I need to turn on this DLP as collector also?
Issue 2:
license: 325 nodes (300 servers/security/network and 5 API: sophos, office365 and 1: AWS cloud trail)
I believed 325 nodes will be installed inside the DLP and but not sure about SH and LC, I think I need to purchase another 3 licenses for the rest so new licenses are 328 nodes. Any advise?
Issue: 3
based on my study/reading info, the LC is a collector also function as normalizer log.
in my case, when the LC act a normalizer? because:- after turn on collector, there is no dashboard etc
- eg: LPA, the configuration for normalizer at the DLP not inside the LC
Thanks for your response.
Regards,
Mohamed
-
Implementation the SMS feature throught LogPoint
Hi,
I’m intressted in implementing the SMS feature through LogPoint. However, to activate this functionality, I need an SMS hosting service. Could you tell me if LogPoint offers an SMS hosting service ? If so, what is the procedure to set up this feature ? If LogPoint doesn’t provide SMS hosting, could you recommend a good SMS hosting service, compatible with LogPoint ?
Thank you in advance.
Siawash,
-
Adding Device to logpoint
Hi,
I had added a device into the logpoint and I have done all the steps of this documentation Devices — Data Integration latest documentation (logpoint.com) .
However, the logpoint didn’t collect any log from this host. In addition I checked in this host and I didn’t find lpagent. Could you please tell why it not works ? And what should I do ?
Regads,
Siawash
-
Phishing and Quishing – Email Investigation and Response Using Logpoint
Email has become an indispensable part of our lives, and the need for heightened cybersecurity awareness has never been more critical. Phishing attacks are among the most common and insidious threats to our online security.
Here are some eye-opening facts that underscore the extent of this global issue.
💰 Shockingly, cybercriminals invest significant sums daily, ranging from $200 to $1000, to orchestrate intricate phishing campaigns, underscoring the immense resources allocated to compromising your security.
🔐 Disturbingly, statistics reveal that over the past six months, users reported phishing attempts only 11.3% of the time. This alarming figure highlights the need for proactive measures against these threats, as a significant number of malicious attempts go unreported.
🚫 The good news is that tech giants like Google are at the forefront of the fight against phishing. They actively thwart around 100 million phishing emails daily, providing a robust defense against these nefarious attacks.
Protect your organization's integrity and safeguard your personal information by delving into our comprehensive guide on how to investigate and respond to email threats effectively 📩
Read the full article here: https://www.logpoint.com/en/blog/emerging-threat/email-investigation-and-response-using-logpoint/
-
Unmasking APT29: The Elusive Cozy Bear Cyber Threat
Warning ! Detect, respond, and manage this active ransomware with Converegd SIEM, AgentX, and SOAR automation playbooks.
Emerging Threats Protection Report
Not Too Cozy: Cozy BearWhat you get:
- Introduction to Cozy Bear
- Free download report from our Security Research team.
- Playbooks: Automate your way to protecting against Cozy Bear.
- How can you leverage your Converged SIEM against Cozy Bear? Download the report.
Here is why this is important. Some Cozy Bear background info:
Fast Facts:
🔍 Aliases : The Dukes, APT-29, Cozy Bear, or Nobelium - whatever you call them, they're the same. We'll use these aliases interchangeably throughout the blog and report.
🌐 A Notorious Background : The Dukes, believed to be linked to Russia's Foreign Intelligence Service (SVR), are a formidable cyber espionage group. Their targets? Governments, NGOs, businesses, think tanks, and other high-profile entities through sophisticated spear-phishing campaigns.
🤺 Unconventional Tactics : The Dukes are known for their unconventional techniques, employing HTML Smuggling and malicious ISO images to deliver malware while slipping past security measures.
🇺🇸 Political Intrigue : APT-29 made headlines by targeting political entities, gaining notoriety for hacking the Democratic National Committee during the 2016 U.S. presidential election.
🌌 SolarWinds Shockwave : APT-29's most significant operation was its involvement in the 2020 SolarWinds supply-chain attack, which compromised multiple sectors of the U.S. government. This event showcased their capabilities and sophistication, making them a force to be reckoned with.
Knowledge is your shield in the ever-evolving world of cybersecurity. With Logpoint's expert analysis, you're not just informed; you're equipped to face the challenges of the digital age head-on.
Join us in the quest for cyber resilience. Dive into the report and fortify your defenses against APT29 and its aliases and read the full report below 🌐
-
The ODBC Enrichment source is not showing up
Hi there
We have Created a ODBC enrichment Source to use a SQL Database for enrichment.
It is all setup on the source side and seems to be working.
But when I then go onto the Director console to add said source in a Enrichment Policy, the source is not there to select, all the other sources are but this one is not.
Has anyone experienced this before?
-
Publish Dashboard to Public API
Hello all,
I am looking for a way to publish a dashboard to the public API. Does anyone know if this is possible?
As it stands I have managed to publish individual dashboard widgets to the public API but I would prefer to share the whole dashboard with 1 URL.
Thanks
-
Logpoint Health monitoring through Grafana
Hi All,
We do have different clients and we want to create a real time monitoring system.
Is it possible to integrate it on Grafana, if yes do you have any idea how?
i know that monitoring through email is possible but we want a centralized monitoring system
Thanks
-
list all event ids found by each device
I need to create a query to export the results with the following criteria, but unsure how to write the query.
I want to list every end device by hostname (including all end devices fed by Windows event collectors, not reported as the WEC) and then all the event codes (unique) collected from that device in ascending order.
Can someone please point me in the right direction
User groups in Zendesk Community allow members to connect, share insights, ask questions, and collaborate within specific interest areas.