Welcome to Logpoint Community
Connect, share insights, ask questions, and discuss all things about Logpoint products with fellow users.
-
LogPoint [AIO] - import syslog from a syslog server
Hello,
I have an archive server were I store some syslog/json logs on. I wonder If It’s possible to send over som of these to LogPoint?
Is It possible manually to transfer over some of the logs from the archive → Logpoint AIO? Like use scp or something else.
I dont find any related documentation related to this. -
Exiration log for Microsoft office 365
Hi,
I would like to know if it is possible to find the log that show the expiration date of Microsoft office 365 account ? If yes, could you please tell me how can I find it ?
Regards,
Siawash
-
Logpoint Agent X Applocker Dashboard
Hi.
We have implemented Agent X into our systems, and we are observing Applocker Events with Agent X.
Now our customer would like a dashboard for these Event.
And I was not sure how to go about creating these Dashboards.
How can I make a dashboard specifically for the Eventviewer logs.
Cheers Mike -
How to estimate the volume of data collected ?
Hello,
I would like to search a query to know the volume of data per day collected in my Logpoint.
Thanks a lot
-
P2P network connection detect rule
Hello everyone,
Being searching LP blogs and community to see if we have any detection rules for P2P network connections. Came out there is a rule to finding P2P applications but nothing of useful to find the network connection. Any tips or suggestions in building a P2P detection will be much appreciated.Thanks
-
Collect DHCP logs & enrichment with other log sources
I’m thinking of onboarding internal DHCP logs. But I don’t quit know yet If it’s a good way to go.
I’m also in the progress of onboarding ISE logs, for authentication monitorering. Is It possible to correlate DHCP logs with ISE logs?
How about use-case related to DHCP logs? Looking at the built in alert rules there was only few use-cases related to DHCP.
I think more about rouge DHCP server and so on.
Does anyone have experience about DHCP logs and the the ability to correlate these with other logsources to get MAX out of It.
Thanks! -
WinRAR – Decompression or Arbitrary Code Execution
Fast Facts
-
With over 500 million users worldwide, WinRAR is the world’s most popular compression tool!
-
CVE-2023-38831 , named ‘RARLAB WinRAR Code Execution Vulnerability is an arbitrary code execution vulnerability on WinRAR, with a CVSS score of 7.8
-
CVE-2023-38831 vulnerability has been patched in the latest version of WinRAR and the vulnerability resides on versions prior to 6.23.
-
Threat Actors have been targeting this vulnerability to deliver malware such as Agent Tesla, GuLoader , Remcos , and Darkme .
Curious to read more and understand how Logpoint’s platform can assists analysts in detecting and responding to security issues? Read the full article on Logpoint’s blog here: WinRAR – Decompression or Arbitrary Code Execution
-
-
LogPoint UEBA Configuration
Hi!
I’m wondering how LogPoints UEBA handle nested AD groups? Nesting of AD groups for selection of specific users that I wont to point to the UEBA cloud for AI intelligence.
Is this possbile?
-
Nxlog configuration, dropping logs from local host on IIS
Hi,
I can’t get this to work, maybe some of you have tried this before.
The drop line below works fine syntax wise, but my goal are to get rid of 127.0.0.1 logs, and when i remove the “!” it fails.
Help Are apprecierede
Regards Kai
<Input IIS1>
Module im_file
File "C:\\inetpub\\logs\\LogFiles\\W3SVC1\\u_ex*"
Exec if $MessageSourceAddress != "127.0.0.1" drop ();
ReadFromLast FALSE
Recursive TRUE
PollInterval 1
Exec $FileName = file_name();
Exec if $raw_event =~ /^#/ drop();\
else\
{\
w3c->parse_csv();\
$EventTime = $EventTime - (2 * 3600);\
$SourceName = "IIS";\
}
</Input> -
Add subnets to list
Hi, how can I paste a list of subnets to a static list?
I'm trying to add a list of subnets to a static list in Logpoint (7.3.2). e.g.:
1.2.3.0/24
2.3.4.0/24
5.6.7.0/23
4.3.2.0/22
I cannot just copy/paste the list as it is pasted as one entry. -
Warning! Detect, respond, and manage this active ransomware with Converegd SIEM, AgentX, and SOAR automation playbooks.
What you get:
- Introduction to Akira ransomware via blog.
- Free download report from our Security Research team.
- Playbooks: Automate your way to protecting against Akira.
- How can you leverage your Converged SIEM against Akira? Download the report.
Here is why this is important. Some Akira background info:
Emerging Threat: Akira, Not a CyberPunk Movie – A Very Real Ransomware Threat
Fast Facts
-
Emerging in March 2023, Akira ransomware has been grabbing daily headlines with its relentless and perilous assaults, leaving a trail of mounting victims.
-
Akira is actively targeting Cisco ASA VPNs without multi-factor authentication to exploit CVE-2023-20269 as an entry point for their ransomware.
-
Akira was among the Top 10 Ransomware groups in August 2023, with no indication of slowing down.
-
Not only Windows, but the Akira variant can also infect Linux systems
-
As of September 6, 2023, they have successfully struck 110 victims , including big-name organizations such as Quality Assistance Leader, Intertek.
Akira has emerged as a tenacious and devastating adversary in an ever-changing field of cyber threats that has grabbed widespread notice in a short period of time. Organizations must adapt and improve their security procedures in this situation. The growing number of people falling victim to this expanding menace emphasizes the importance of the situation.
Logpoint's security operations platform, Converged SIEM, contains a range of extensive tools and capabilities for identifying, evaluating, and mitigating the impact of Akira Ransomware. With features like native endpoint solution AgentX and SOAR with pre-configured playbooks, it enables security teams to automate essential incident response procedures, gather vital logs and data, and expedite malware detection and removal operations.
In an ever-changing threat landscape, Logpoint gives organizations the tools and capabilities they need to monitor risks, build defenses, and protect against Ransomware activities like Akira.
SOAR is always included in your Logpoint subscription. Not set up to use SOAR? Reach out to your local Logpoint representative or customersuccess@logpoint.com to hear how we can get you started.
Did you download the report? If so we would like to hear from you. Send us a message below and let us know your thoughts. What did you like? How can we improve it?
-
Access individual logs within single stream
Hi,
I want to display all relevant information that is available for remote sessions per remote session. However this is contained in different logs that all have the same session_id. Suppose I gather those logs in a search via a single stream. For example like this:
[3 user=”x*” type=login OR type=logoff OR type=authentication_try having same session_id] as StreamHow can I access the individual logs included?
For example
| fields Stream.type, Stream.col_ts, Stream.user or
| chart count() by Stream.user etc. doesn’t work.
Just showing the fields without grouping of same session_id is not the solution, since I cannot order fields and all session_ids are mixed.
Hope there’s a way. Best
Georg -
group logs with same value
Hi everyone,
Here is a task that puzzles me: I am looking at events of remote connections and I want to display the connections that are currently active. One Connection has evetns like “login”, “authentication_try”, “session_closed”, etc. and the same session_id. The number of logs with the same session _id may vary, since, for example, there might be more than one authentication_try.
So I would like to first group all events with the same session_id and then filter out those, that do not have a “session_closed” event.
I tried to implement this with one or two streams (join) but did not come to a solution. With one stream I cannot give an exact number of logs “having same session_id”, with two streams I would need something like
“[session_id=*] as first-stream
join[session_id=*] as second-stream
on first-stream.session_id=second-stream.session_id AND first-stream.log_ts!=second-stream.log_ts”. Also a “not followed by” could have been a solution for this, which does not exist.
Does anyone have an Idea how to accomplish this (without using a Playbook).
Best regards
Georg -
Dynamic Alert Recipient
Hi all,
i would like to send an email alert and choose the recipient depending on the triggered alert. For example, when a user changed his active directory password, i want to send him an email, telling that the password for his account was changed and if it was not himself he should contact directly the helpdesk.
Best
edgar
-
Re-parse an event for normalization (JSON-event)
Hi !
Just a interesting question. I know that other SIEM vendors have problem with this. Maybe LogPoint have a good function for this.So I received a JSON-event that didn’t normalise, due to that no normalization-package was enabled. I enabled this after I received the event.
So to my question. Is It possible to parse this event afterwards so that It gets normalized? Or do I have to wait for another event from the same logsource to see If this one gets normalized? -
Sylog message sizing
Hi
What are your opinions on increasing the size of the syslog message.
Increasing syslog message size will potentially have a negative impact on the performance in log collection, normalization and parsing.
On the other hand it is important to be able to extract the necessary information from collected log messages, and some windows evenLog messages have increased over time.
Take for example event ID 4662 ‘An operation was performed on an object’, it can exceed 34000 in message size.
Another example is custom application logs, where developers might have another opinion, of what meaningful logs should contain.
Regards
Hans
-
Defending Against 8base: Uncovering Their Arsenal and Crafting Responses
The 8Base ransomware group initially surfaced on the cyber threat landscape in March 2022, and their activities significantly increased in June 2023. They notably target small and medium-scale industries. While their actions began in March 2022, it wasn't until May 2023 that a substantial increase in their activities became apparent. This placed them among the top 5 most active ransomware groups in both June and July 2023.
In the realm of ransomware activities, our focus has unwaveringly remained on various groups and their activities. As the calendar rolled into July, the emergence of the 8Base group took a significant turn as it secured the 3rd position among the top 5 ransomware groups. As it continues to widen its range of victims and expand its operations, the group poses a growing threat solidifying its position as a potent adversary in the ever-changing cyber threat landscape.
In the report you can read more about the Logpoint Emerging Threats Protection as well as recommendations to keep your environment more secure against various threats.
-
Collector not pushing to data node
Hi,
I have a distributed system with dedicated collectors. Now, during setup and configuring a few hundred linux servers via rsyslog to send their logs to one collector, the collector suddenly stopped pushing the data further to the data node. I’ve rebooted the collector, which resulted in temporary relief, however after roughly two hours, the problem resurfaced.
Using tcpdump on the collector I can see logs streaming in from the log sources (tcp/514), and also on the data node I see openvpn-udp traffic comming in from the IP of the collector - not sure however if in latter I see only tunnel keepalive traffic, as the packages are very small 65-103 byte.
I don’t have a clue on how to understand what is going on and where to look at - seems some resource problem to me, in terms of memory or cpu the system is well equipped and bored :-).
The thing is, when doing a search over all repos with "collected_at"="myCollectorName" I don’t get any data at all. As if the thing would not exist.
Do you have ideas how to analyze this better?
Thx,
Peter
-
Integration with Salesforce Commerce Cloud
Does Logpoint has out of the box integration with Salesforce Commerce Cloud? Has anyone did this from this group? Appreciate if you could help!
-
Launch a playbook when an alert is triggered
l have an alert rule that triigers when it detects a web attack like XSS, SQLI.
i want my playbook to starts when the alert is triggered.
Any idea??
-
Logpoint Agent X and devices Hostnames
Hello
with the new Agent X, we were testing adding Devices with Agent X to logpoint, due to DHCP they will not always have the same IP address. We attempted to add this device via Hostname to logpoint, but even though the Agent X panel claims that it is active and collecting logs, When searching for said logs, I get no result for the Hostname.
Is it Possible to use Hostnames to add Devices to logpoint in use with agent X?
Or is it not possible. -
Information about Disk Storage
Hi,
I am reaching out to you regarding an issue I'm experiencing with the disk storage logs. It seems that for the past week, I have not been receiving any logs pertaining to disk storage. I would greatly appreciate it if you could kindly inform me about the possible reasons behind this.Thank you in advance.
Siawash
-
Have anyone tried to get logs from Kubernetes, maybee a best pratice.
I see that there are no Vendor Apps for Kubernetes, so normalization are maybee going to be written, but how do you get logs to Logpoint, are there a nativ way for this.
I found that Auditing of logs are not default turned on, and if they are they only reside for 1 hour.
Any one with some god advise in the matter ?
Regards Kai
-
Help-Query for user logged into multiple systems
Hi,
I am looking for a query for finding ‘users logged into multiple machines’. Can someone please help me out.
Thanks in Advance,
KP
-
[HOW TO] plot something other than the frequency in search
Dear fellow LogPoint users,
I would like to plot a given quantity over time in search and in my dashboards. For example, the GBs of data transferred over time, or the values of a time table. To my understanding chart, as well as timechart does not allow this. These functions only aggregate the number of occurences within the given time-interval (like in a histogram).
Is there a way to do this?
Best regards,
Georg -
how to compare different times in search
Dear fellow LogPoint users,
I am wondering if there is the possibility to compare the results of a querry for different times in one plot?
This would be very helpful to identify regularities/irregularities. For example, the number of logs received today over the number of logs received yesterday and the day before. Yes, I can create a dashbord and stack the corresponding widgets on top one another. However, it would be helpful to be able to directly compare the curves in one plot.
Thanks in advance
Georg
-
A playbook that streamlines the process of investigating incidents associated with a specific IP address
Hey everyone,
During my day to day, I identified a workload that I was able to fully automate with SOAR playbook.
I have created a SOAR playbook that does the following.
Takes the outbound IP address from incident data as a trigger. In my example, 213.183.58.12.
The playbook automates the following workload.
- Checks WhosthisIP to gather information about this external IP (domain, etc)
- Uses SearchAPI to extract all users that have interacted with this IP (from SIEM). Also extract all the incidents related to the above IP
- Uses SearchAPI to get the number of incidents this user is associated in the last 12 hours
- Sends an email to the required address (completely customisable) with the list of those incidents info (this could be your SOC's email, or analyst's email) and waits for response
- Use IncidentAPI to mark this incident as resolved and Close the Case, when the email gets an response.
This playbook can be nested with other playbooks or you can run it independently. Please be aware that when you run it independently, it will create a case item.
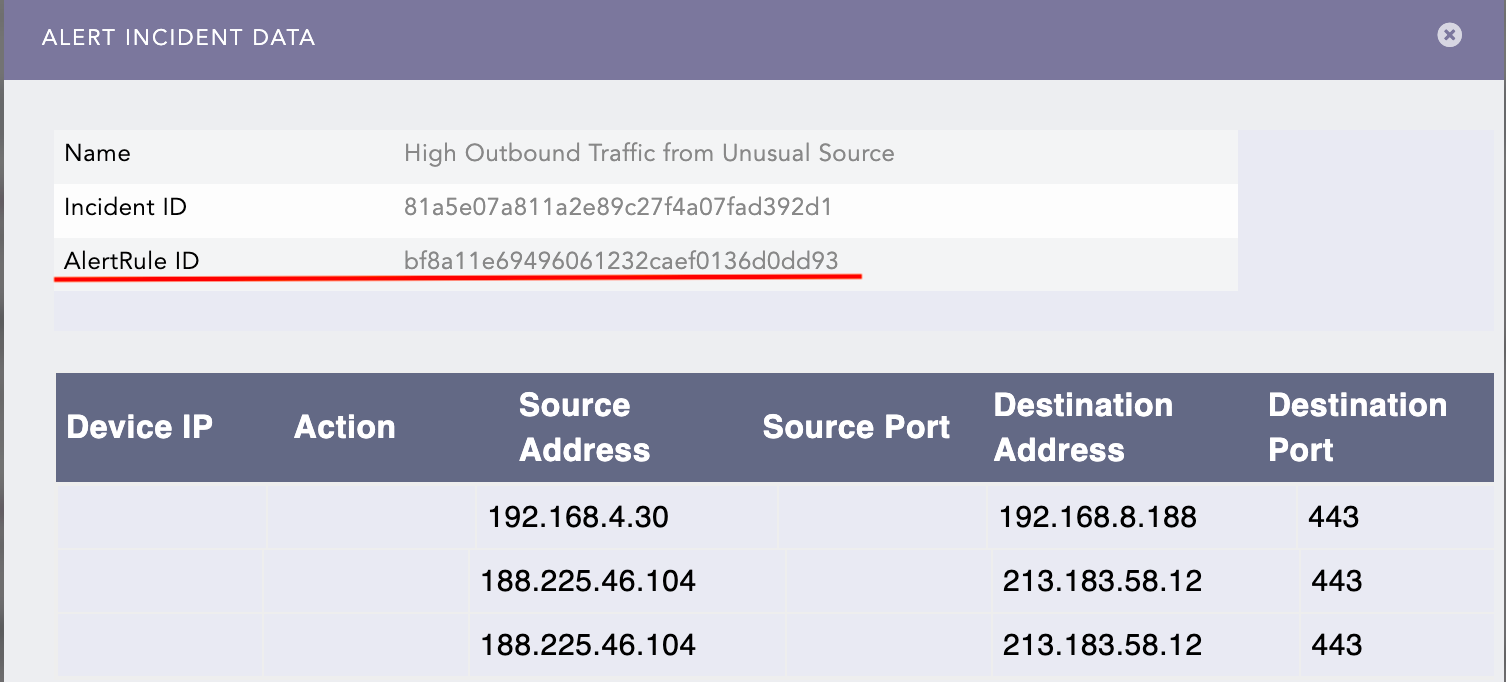
Do try and let me know what you think. Please feel free to modify and add other interesting workflows that can be automated, and share back.
Niklas
-
Login Unknown User Formant Alert Rule
Hello
Our company very recently configured a Logpoint for ourself and a Customer.
the Customer asked for a alert rule, to Alert us and them, whenever someone Attempts to login with a Unknown username format. To see those attempts and see if someone accidentally typed their Password in the username Field.for this I created this rule (there is probably better ways to do this)
-("source_address"="ip") -("source_address"="iü") -("user"="du*") -("user"="MINWINPC") -("user"="ch*") -("user"="firewall") -("user"="aa*") -("user"="da*") -("user"="nu*") -("user"="su*") -("user"="la*") -("user"="cba_anonymous") -("user"="ex*") "reason"="Unknown user name or bad password." "event_category"="Logon" device_ip=ip or device_ip=ipThe Rule ended up being pretty long, but it mostly works.
The mostly being that it generates a lot of noise, because there is a lot of Alerts with user Null, so empty, these alerts seem to come from the DC itself.
And I am trying to Exclude null from the search.
I tried.-(“user”=”null”), -(“user”=”NULL”), -(“user”=”*”) and -(“user”=*)
but none of them actually excluded null.Does anyone Know or have an idea on how to Exclude null results in a search, that would be a great help.
Also open for more efficient ways for the rule since it is really loong haha.
Thanks in advance Cheers Mike -
PowerExchange Malware backdoor - Exchange servers
Hi!
Is there anyone in this community thas has some knowledge about the recently malware backdoors on Microsoft Exchange servers?
I would like to investigate this further and do some threat hunting. Does anyone here has some threat hunting querys in LogPoint?
-
Supported Python Libraries
Hi folks,
Just a quick question - I was wondering what the available libraries are when using a Python script? Is it just the ‘core’ or ‘standard’ Python libraries available, or is it possible to use third-party ones. I’m assuming that LogPoint doesn’t automatically fetch libraries if you put the import statements in.
In which case, is there any way around this (allowing for pip installs) or would we need to create a separate Python application outside of LogPoint and interface with that (either via API or some other means)?
User groups in Zendesk Community allow members to connect, share insights, ask questions, and collaborate within specific interest areas.