Welcome to Logpoint Community
Connect, share insights, ask questions, and discuss all things about Logpoint products with fellow users.
-
Firewall Use Cases V1.0
Hi All,
In this second instalment of the Use Case catalogue series, we are focusing on Firewalls. Firewalls are a vital part of most organisations and enterprises today. In this Use case catalog you will find a collection of analytics available for firewalls in Logpoint SIEM for PaloAlto, Cisco, Fortinet and Check Point firewalls.
-
Hunting LockBit Variations using Logpoint
LockBit has been implicated as the most active ransomware and has been involved in the most attacks compared to others of its kind. Read our latest blog by Anish Bogati & Nilaa Maharjan from Logpoint Global Services & Security Research on how Logpoint can help you to strengthen your security posture when it comes to LockBit ransomware.
Link to the blog post:
https://www.logpoint.com/en/blog/hunting-lockbit-variations-using-logpoint/
-
Introducing: Certified Logpoint SOAR Training
We are delighted to announce the launch of our new Certified SOAR User Training.
Throughout the full day training session, a LogPoint Certified SOAR Expert will display and explain the features of the SOAR solution, look into real-world use cases, highlight best practices and how all the various blocks of Logpoint SOAR can be combined for maximum efficiency.
The first course debutes on October 24th, and will recur monthly. (For the other upcoming dates, please see below.)
For further inquiries about registration and pricing, please contact your local Logpoint representative or email to csz@logpoint.com
Course Schedule Q4 2022 / Q1 2023:
- Monday October 24th 9 AM-5 PM CET
- Monday November 28th 9 AM-5 PM CET
- Monday December 12th 9 AM-5 PM CET
- Monday January 23rd 9 AM-5 PM CET
- Monday February 20th 9 AM-5 PM CET
- Monday March 20th 9 AM-5 PM CET
For more information, please visit logpoint.com/LogpointAcademy
*All courses are held online
-
Save the date for ThinkIn 2023
We are excited to announce the date for our ThinkIn 2023 conference for global Logpoint users and partners. Here’s some key info:
Copenhagen, March 7-8, 2023 @Crowne Plaza Copenhagen Towers
As we are currently working on the official agenda, we encourage you to share your ideas on what kind of workshops and keynotes you would like to participate in.
All ideas are welcome in the comment section below or via email to customersuccess@logpoint.com .
Participation is free of charge. So all you have to do is get to Copenhagen and find a place to stay. Simple!
We are looking forward to seeing you.
Click here for pre-registration
-
Introducing the Logpoint Use Case Catalog
Focusing on one use case at a time, the Use Case Catalogue will guide you through the implementation of basic monitoring of specific log sources in a Logpoint SIEM platform. The first instalment of the Use Cases Catalog series, Active Directory Use Cases is now available on the link below: https://community.logpoint.com/active-directory-13
-
CSV Enrichment Source v5.2.0 is now publicly available
Dear All,
We are happy to share that we have released CSV Enrichment Source v5.2.0 publicly.
The CSV Enrichment Source application enables you to use a CSV file as an enrichment source in LogPoint. The application fetches data feeds from a CSV file and enriches search results with the data.
For further information, please visit the link below:
https://servicedesk.logpoint.com/hc/en-us/articles/115003786109
For detailed information about the implementation in Logpoint products, please refer to the articles below:
- Logpoint: https://docs.logpoint.com/docs/csvenrichmentsource/en/latest/
- Director API: https://docs.logpoint.com/docs/csvenrichmentsource-for-director-console-api/en/latest/
- Director Console: https://docs.logpoint.com/docs/csvenrichmentsource-for-director-console-ui/en/latest/
-
Qualys vulnerability management integration
Hello,
We’re looking at integrating our Qualys VM scans into our Logpoint instance. I was hoping to pick someone's brain about this. Does this only work on singular Qualys accounts, or will it work on MSSP/Consultant editions?
Many thanks,
-
Incident Reporting Overview with Search Query
Hi,
I have been looking into how to get an overview over actions taken by an Security Analyst whilst using the Incidents view on Logpoint.
Therefore i have created this Search Query to get an overview over Incdents and Actions.
Repository to be searched on is _LogPoint
incident_id = * | chart count() by incident_id, log_ts, alert_id, status, action, user, alert_name, comment order by incident_id, log_ts asc
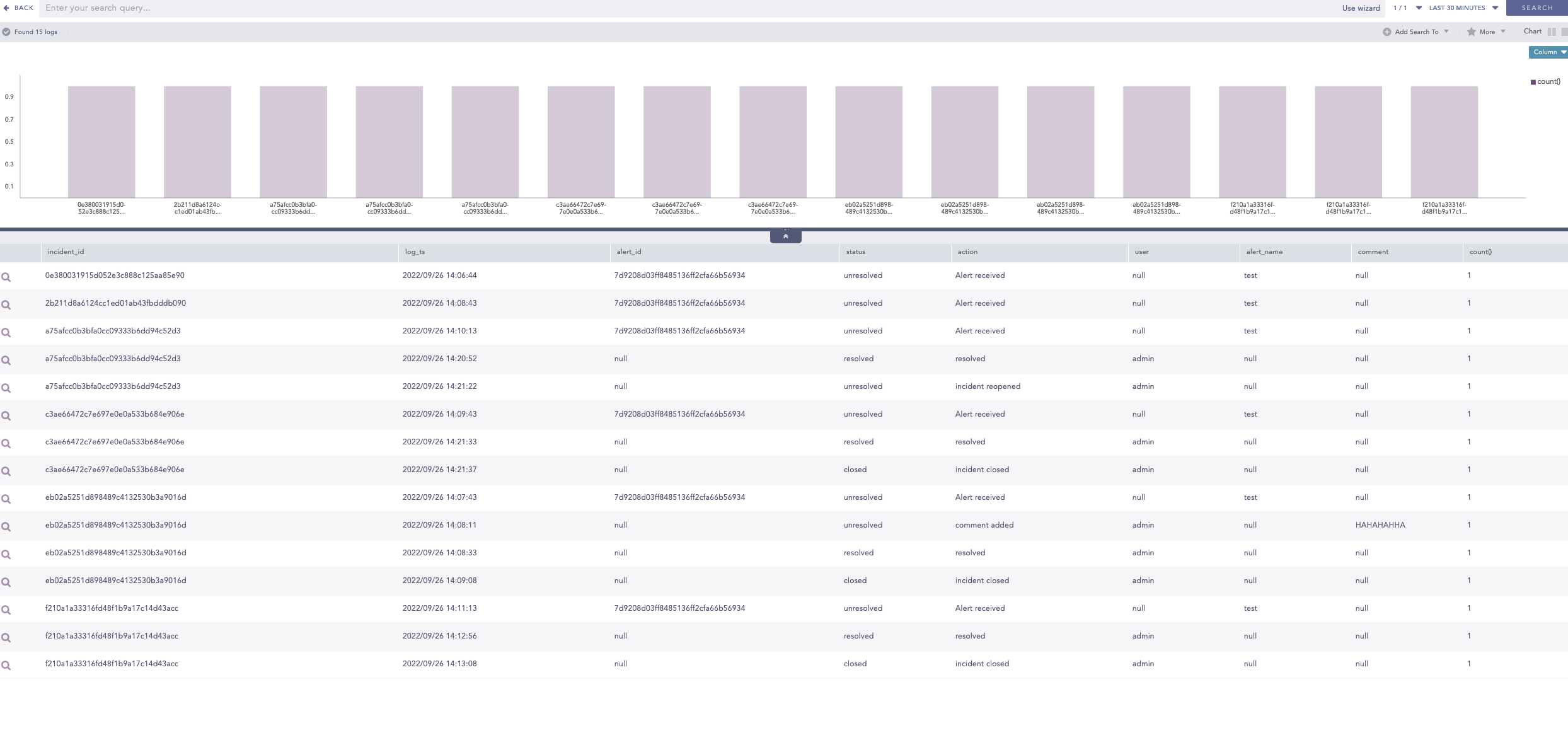
Hope this could be useful.
Best Regards,
Gustav -
Enrich DHCP Logs, With ISE Cisco Logs. To see Switchports
Hi there.
So we Have a Alert rule, that alerts us when a Unknown and New Device, leases a DHCP Adress, to prevent unwanted Physical Access.
Now We wanted to Enrich said DHCP log, by adding Information of our ISE/Switch Logs, so that when we get the Incident from the Alert rule, we also see what Switch and Switchport, this Unknown device is Hanging at.
We are Pretty sure that should be Possible, but I haven’t figured out how yet.
Cheers Mike Furrer -
Rename a case within a Playbook?
Hi folks,
Another cases and playbooks question - is there a way to update the name of an existing case item from within a Playbook?
By default, we are generating cases with just the incident ID for identification, but we’d ideally like to be able to update the name of the case once some additional playbooks have run.
We already have a way to get the case ID etc, it’s just the renaming part we’re stuck on.Is this possible?
-
Idea Portal. Update on visibility and not only
We recently updated our Idea Portal to bring even more privacy and freedom of sharing ideas - for example, it’s no longer showing names of the users voted for the idea, even names of the users commenting it. That should help to preserve anonymity even when ideas are created from the support ticket.
Our team plan to continue improving experience of all “ecosystem” resources like Idea Portal, Service Desk and so on - so we appreciate any feedback from the community about this change - or any other potential changes. Please feel free to comment there - or by any other channel.
NB: limited set of Logpoint employees, product managers with sufficient permissions, can still see names of the commentators in the back office of idea portal - to enable direct dialog on any specific feature scenario to be discussed outside idea portal.
-
Detecting devices that are not sending logs
Receiving logs is one of the cure features of having a SIEM solution but in some cases logs are not received as required. In our newest KB article, we are diving into how to monitor log sources using Logpoint alerts to detect no logs being received on Logpoint within a certain time range.
To read the full article, please see the link below: https://servicedesk.logpoint.com/hc/en-us/articles/5734141307933-Detecting-devices-that-are-not-sending-logs-
-
Update case with output from Playbook
Hi folks,
Is there a way to update a case with the output of a Playbook?
For example, if I have a Playbook that checks an IP Reputation, is there any way I can get the Playbook to update the case to display the reputation response as an actual Case Annotation or something of the sort?
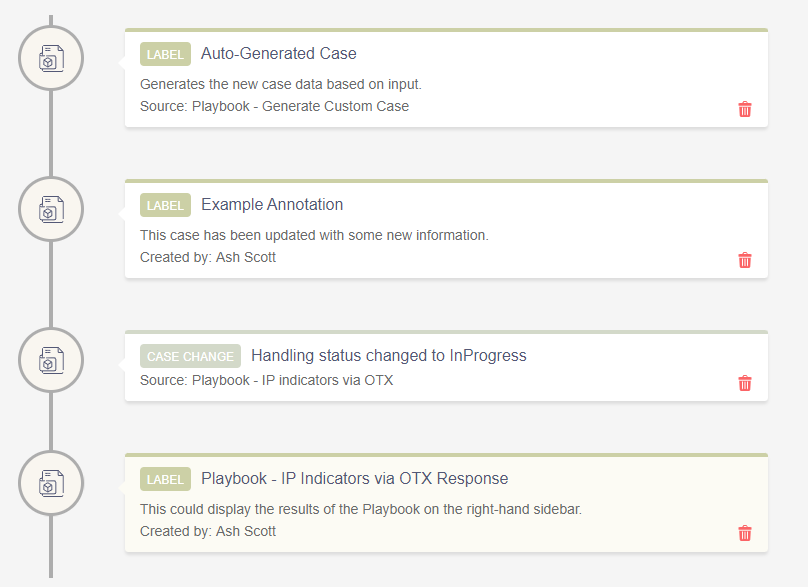
-
Passing parameters within a Playbook Trigger?
Hi folks, I’m trying to set up a Playbook Trigger, but wanted to potentially pass through parameters for it.
The setup is as follows:
- Alert is triggered
- Playbook Trigger runs based on matching alert_id
- Playbook generates case data and runs additional actions/playbooks.
I would (ideally) like the Playbook Trigger to pass details from the incident to the Playbook it is linked to.
Is this something that’s possible from the Trigger directly, or do I need to use a Query/another action within the Playbook to try and extract the info I need?
On that note, is there an easy way to get data from the incident that triggered the alert within the playbook itself?
-
LogPoint SIEM HDFS support and configuration
Hi,
does Logpoint support HDFS do store data e.g. on an DELL ECS object storage?
If yes, how must this be configured in best practice?
Thanks.
Best Regards,
Johann
-
Understanding file_keeper Working and Configuration
The `file_keeper` service, primarily used for storing raw logs and then forwarding them to be indexed by the `indexsearcher` is often used in its default configuration. However in some real life situations this might not be sufficient to deal with the type, and volume of logs being ingested into LogPoint, hence tuning is required. In our newest KB article, we´re gonna guide you through how exactly to do it.
For more details, please read the full article on the link below:
-
Where the to find detail about type of log can be collect from different device
Hi,
I want to know the information about all the data/logs that will be captured by LOGPOINT SIEM from different devices such as Firewall the logpoint SIEM can captures is syslog. So how about the others supported device/sources such as workstation /switches ? and where in Logpoint site/portal that we can to find this info?
Actually we want to list out detail for every device that can give us easy to forward log to logpoint siem.
-
Integrating the logs from kaspersky
we need to send the kapsersky logs into logpoint. we have configured the kapsersky to send events to logpoint machine through syslog port 514 and protocol is UDP, but it does not send the logs. need help.
-
User account privileges escalation
is their a method or can their be method, where you can set your user accounts in log point as standard account, when someone need to complete any administrative task a ticket/token can be raised, with time frame limit. where manager/third person can either approve or reject it request to escalate current of the user account from standard to admin. For account tracking and better account visibility. Just as in Microsoft 365 security or MDE security portal.
-
Release of CloudTrailv5.1.0
Dear all,
We´re happy to share the public release of CloudTrailv5.1.0
Please see the details on the link below:
https://servicedesk.logpoint.com/hc/en-us/articles/360000219549
-
New applications available with Logpoint v.7.1.0.
Hi All,
We´re happy to share that we have released the following applications on the Help Center:
- Experimental Median Quartile Quantile Plugin v5.0.0
- Vulnerability Management v6.1.1:
- Lookup Process plugin v5.1.0:
- Logpoint Agent Collector V5.2.2
- Universal REST API Fetcher v1.0.0
All applications have been bundled in Logpoint v7.1.0 and are available out of the box.
-
A Spool’s Gold: CVE-2022-21999 – Yet another Windows Print Spooler Privilege Escalation
Hi All,
SpoolFool, also known as CVE-2022-21999, is a local privilege escalation flaw in Microsoft Windows’ print spooler service, which controls print operations. Read Logpoint´s take on it along with detailed steps to protect your organisation in the article below, written by Nilaa Maharjan.
-
Top 5 SOAR use cases
Analysts are constantly swamped with alerts, and to deal with this, they have to rely on repetitive manual tasks. This is like putting water on an oil fire, making the situation much worse and more time-consuming.
SOCs need a solution that enables them to manage and prioritize their workflow efficiently by giving them the ability to collect security threat data and alerts from multiple sources. This is where Logpoint steps in.
Previously we identified top use cases for SIEM . This time here are five common SOAR use cases that every organization should implement to reduce alert fatigue, overload and subsequently increase productivity in your SOC team.
01 Automated alert triage and enrichment
02 Endpoint malware mitigation
03 Automated Phishing Investigation and Response
04 Automated Threat Intelligence management
05 Ransomware mitigationTo read the full story, read the link below: https://www.logpoint.com/en/blog/top-5-soar-use-cases/
-
Monitoring Alerting Services
Hi All,
Alerting is one of the core feature of Logpoint, in the article below we collected a compact list of the precautions that can be done to ensure that alerting runs smoothly and what to do if you realize the alerts weren't triggered.
To read the full article, please follow the link below:
https://servicedesk.logpoint.com/hc/en-us/articles/6013024248093-Monitoring-Alerting-Service
-
Common Issues in Normalized logs
Hi All,
Our latest KB article discusses common issues where logs seem normalized ( both norm_id and sig_id are present), but some problems prevent them from being used in analytics.
To read the full article, please follow the link below:
https://servicedesk.logpoint.com/hc/en-us/articles/5830850414493-Common-Issues-in-Normalized-logs
-
Resolving timestamp related issues in Normalization
Hi All,
Sometimes we face an issue like an alert not being triggered or a dashboard widget not being populated. There could be many possible reasons. Among them, one is a huge time gap between log_ts and col_ts . In this article, we will be discussing some of the possible causes and sharing tips and tricks to solve this.
Please see the link to the article below :)
-
max amount of Repos
Hello Guys,
is it possible to use/create 16 repositories per LogPoint environment only?
What if I like to separate my data in 30 different repositories for managment and access right purposes, is there a way to do that and are there benefits or drawbacks for this situation?
Thanks in advance.
BR,
Sascha
-
New in Knowledge Base
Hi All,
I would like to draw your attention to a recently released KB article discussing things that need to be looked into if the connection from the collector to backend server isn't being created while working with distributed Logpoints.
To read the full article, please follow the link below:
-
Show Alert Detail within the search
Hello Guys,
Is there a possibility to show the “Alert Details” within a search, so we can execute filtering and combining with other searches to get a special reporting on this infomation?
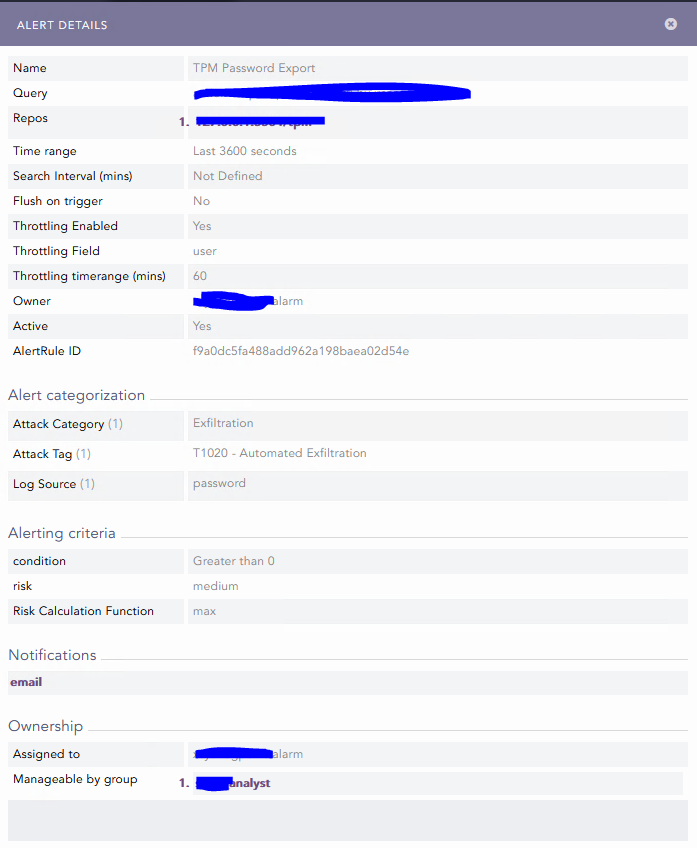
Alert Details -
Search for configuration within the search bar
Hey,
Iam searching for a possibility to return the configuration of defined alert rules in the logpoint search tab.
Background: I would like to report over icindents which are created by alert rules for a specific user group. We got several test alarms, which are “managed” by an other user and which should not appear in the report. So I have to combine the configuration of alert rules and the results with “repo_name="_logpoint" action="Alert received" | chart count () by alert_name, risk_level”.
Unfortunately I could not find a way to bring up the alert rule configuration with a search and combine the result with another search to narrow down the alert rules which I need to report. (I dont want to do that manually per hand by tyoing the names in the search)
I came over this idea because I have done such things with Splunk in the past. (was like an API-Call within the search bar to return internal configuration parameters)
Is it even possible to get the configuration of the XXX back as a json/xml (or other) string?
Thanks in advance.
BR,
Sascha
User groups in Zendesk Community allow members to connect, share insights, ask questions, and collaborate within specific interest areas.