Welcome to Logpoint Community
Connect, share insights, ask questions, and discuss all things about Logpoint products with fellow users.
-
Unable to hunt down the user/process that failes to authenticate on DC
I monitor for failed authentications on DC’s.
labels: Authentication | Fail | Kerberos | User
My top failed authentications is on one client/one account that I can’t hunt down. I have looked at all process’es and their “credential’s” + installed sysmon on the client. But I can’t find the process or user. Any ideas how I could hunt this down?
-
Capture Raw Logs into SOAR Parameter
Is there a way to capture raw logs and use them as field parameter?
-
Jira Integration in LogPoint
Hi team,
Has anyone integrate Logpoint SOAR with Jira’s incident management?. The goal is to have two way integration with LP incident to work with Jira’s ticketing system.
-
Cisco Firepower logs not normalized
Hi!
Been struggling with the normalization of Cisco Firepower logs, were I expect better normalization and a better enrichment. The syslog is configured from the Firepower Management Center.
Everything should be correct in LogPoint were we’ve put in all the normalization policys for the log source.
Compiled Normalizer:
- Cisco FirepowerNormalizer
- CiscoPIXASACompiledNormalizerNormalization Packages:
- LP_Cisco Firepower
- LP_Cisco Fiirepower Management Center
- LP_Cisco Fiirepower Management Center v6_2- LP_Cisco PIX/ASA Generic
- LP_Cisco PIXASA
Is there any problem with the format syslog? Had the same issue with CheckPoint FW, but this got solved when we changed the format to CEF. Only the problem that Cisco Firepower only support the format syslog.
Is there someone that has any tips on how to move on forward with this? -
FileRecycled
Hi!
I have a question about signification “ FileRecycled ”. In fact, in my dashboard I see action= FileRecycled but I can’t understand what exacly it means ! Could please explain me what it means ?
Thank you in advance for your reply.
Best regards,
Siawash
-
Windows SCCM send logs to LogPoint
Hi!
I’m curious into how to collect logs from SCCM. Logs related to endpoint protection, virus alarms, quarantind threats etc.
Found out that nxlog provides a configuration file for this. Missing some fields in the configuration file, example <Output out_syslog>. To point out the syslog dst.Microsoft System Center Configuration Manager :: NXLog Documentation
Has anyone any experience about this?Thankful for replies.
-
how to add remote logpoint through distributed logpoint feature?
Hello community,
I am trying to create a connection between two logpoint server. I followed the documentation but I failed to create a connection.
First, I created the open door on the remote logpoint and then tried to create a connection from another logpoint server using distributied logpoint feature after entering ip, password and private ip. I get a notification stating its already exists but I don’t see new connection in a list,to a remote logpoint server under distributed logpoint.
I further notified IT team to open prot 1194/upd but still no success.
IT team can not see any attempts I have made to connect two logpoint servers on their firewall.
I would appreciate assistance if anyone in the community have tried this or knows how do it. I had a session with LogPoint but resulted in unsuccessful attempts.
thank you very much.
Ranjan
-
Cisco Stealthwatch send syslog to LogPoint
Hi!
I’m wondering If It’s possible to configure Stealthwatch to communicate with LogPoint. I want Stealthwatch to forward events, even better If It also can forward flows to the SIEM.
Is this possbile?
All I can find regarding this is the integration with LogPoints SOAR to configure different types of actions.
Adding the Vendors — Cisco Secure Network Analytics (Stealthwatch) SOAR Integration latest documentation (logpoint.com) -
About director console
can you share some useful commands used in backend for our knowledge like how to find installed version of director console etc..
-
New Logpoint 7.2.0 is ready
The 7.2.0 version is out. Read about it here: https://servicedesk.logpoint.com/hc/en-us/articles/10065818192669-Logpoint-v7-2-0 .
During April, Logpoint will host a Webinar giving more insights into the new features. Look for it in your e-mail inbox or here on the Community
/ Brian Hansen, Logpoint
-
Alert rule with multiple streams and Jinja template not working?
I’ve built a search query that joins two streams/searches.
In the end I do some processing, and rename fields as needed, in my alert I added the renamed fields in my Jinja template, but when I receive the e-mail the fields come up blank.
My rule looks a bit like this:
[..] as s1 followed by [..] as s2 on s1.user=s2.user | process geopip(s2.source_address) | rename log_ts as tidspunkt_ts, s2.user as bruger, s2.machine as computernavn, s2.os_version as OS, s2.source_address as IP, country_name as land, city_name as 'by'My e-mail notification looks like this:
Subject:
{{alert_name}} - {% if rows|length is gt 1 %}{{rows|length}} users connected{% else %}{{rows[0].bruger}} connected {% endif %}Message:
{% for row in rows %}
<ul>
<li><b>Timestamp: </b>{{row.tidspunkt_ts}}</li>
<li><b>Brugernavn: </b>{{row.bruger}}</li>
<li><b>Brugerens Computernavn: </b>{{row.computernavn}}</li>
<li><b>Brugerens OS: </b>{{row.OS}}</li>
<li><b>Brugerens IP: </b>{{row.IP}} ({{row.land}}, {{row.by}})</li>
</ul>
{% endfor %}The search works fine, the jinja template does see 9 elements in the list, my template is repeated nine times, but the place where the property should appear contains no text.
Am I missing something obvious or does the rename command not effect the output to the Jinja template?
-
j
.
-
Emerging Threats: AgentTesla – A Review and Detection Strategies
AgentTesla [ S0331 ] a.k.a Negasteal is a
.NET-based Remote Administrator Tool (RAT) first detected in 2014. It is advertised as a Remote Administrator Tool since then. AgentTesla allows adversaries to remotely control the systems of victims and manipulate them accordingly, so it is utilized by numerous threat actors such as SILVERTERRIER , SWEED , Aggah , and many more.Learn more about the analysis, detection, and mitigation using Logpoint SIEM+SOAR in our latest report on the link below.
https://www.logpoint.com/en/blog/agentteslas-capabilities-review-detection-strategies/
-
New Ideas in Ideas Portal
Hello together!
I hope you all look regularly in the idea portal?I have submitted some ideas that I wanted to draw attention to here:
-
Separate SOAR from SIEM Installation- and Update Packages
The update and installation packages have grown in size a lot since SOAR was introduced. The idea asks to un-bundle the SOAR package so that you don’t have to transfer and install 1.5 GB of update package, while the SOAR uses 1.4 GB of it. -
Preselect Dropdown Values if there is only one option
In the UI there are some dropdowns where usually you have only one selection option. If so, this should be preselected, so you can save some click-work. -
Implement Overview for Live Searches
It would be helpful to know how fast the responses of the live searches in your system are available to estimate which live searches can be optimized or consume the most resources. -
Director: Add configuration object overview and filtering
In the Director Console UI we need a better overview of all available configuration objects. My idea: Show everything (all devices, policies, etc.) in one table and add some filtering options so you can filter pool, machine, object type (device, policy,...). -
Director: Show all relevant information of devices in one simple overview
The device listing so that all relevant information about a device is visible at a glance. If a device has several values in some fields (e.g. several collector apps), then these should be displayed in several table rows or in a different but clear way. -
Director API for Director SSH Commands
It would be good if it was possible to run SSH commands on specific pools and machines via the Director API.
Feel free to add more of your Ideas here. Maybe we can start a discussion here about interesting topics.
-
Separate SOAR from SIEM Installation- and Update Packages
-
Onenote Malicious Attachment as Initial Vector – Detect, Investigate, and Remediate using Logpoint
Attackers are using OneNote files to infiltrate systems by embedding malicious payloads, with OneNote becoming a popular option after macros were disabled.
The attack is not new, with techniques ranging from phishing to sharing OneNote files, and payloads including RATs and information stealers.
To detect and respond to these attacks, it is recommended to check strings of .one files, monitor OneNote’s child process executions, and check for suspicious use of built-in Windows binaries. Windows and 7-Zip have fixed bugs that allowed malicious file formats to bypass security warnings.
The report explores how this attack works and its potential longevity.
https://www.logpoint.com/en/blog/onenote-malicious-attachment-as-initial-vector/
-
ESXiArgs Ransomware: never too early to jump the gun
Hi All,
We are excited to share our latest blog on ESXiArgs Ransomware by Logpoint Security Researcher, Bibek Thapa Magar.
VMware ESXi hypervisor allows organizations to host multiple virtual systems on a single physical server. A global ransomware campaign named “ESXiArgs” is targeting VMware ESXi servers and exploiting a two-year-old vulnerability (CVE-2021-21974). The involvement of other CVEs has been speculated. In October 2022, a custom python backdoor was detected on a VMware ESXi server, which could run remote commands or launch a reverse shell. This backdoor may have a role in the infection routine.
Get research and analysis, insight, plus hints and tips, on how to mitigate ESXiArgs in the main blog below.
-
How to Extract Custom SAP Table Modification Logs in SIEM Using LogPoint for SAP?
Hello everyone,
I hope this post finds you well. Today, I'd like to discuss how to extract custom SAP table modification logs in SIEM using LogPoint.
For those unfamiliar with the concept, SIEM (Security Information and Event Management) is a technology that combines security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by network hardware and applications.
LogPoint is an industry-leading SIEM solution that enables users to collect and analyze log data from various sources, including SAP systems.
When it comes to SAP systems, LogPoint can be used to extract modification logs for standard tables. However, for custom tables, some additional configuration is required to ensure that the logs are collected and analyzed properly.
Here are the steps you can follow to extract custom SAP table modification logs in LogPoint:
Step 1: Enable Change Document Object
First, you need to enable the change document object for your custom table. You can do this by using the transaction code SCDO. Once you have enabled the change document object, SAP [ https://www.lenovo.com/ca/en/servers-storage/solutions/sap ] will start creating logs whenever a change is made to your custom table.
Step 2: Define Change Document Object for Logging
Next, you need to define the change document object for logging. You can do this by using the transaction code SCU3. In the Object Attributes tab, select "Change Documents" and then choose the "Create/Change" option to define the change document object.
Step 3: Define Logical System Name
Now, you need to define the logical system name for your SAP system. You can do this by using the transaction code SALE. In the "Logical Systems" option, select "Define Logical System" and then create a new logical system name.
Step 4: Configure the RFC Destination
Next, you need to configure the RFC destination. You can do this by using the transaction code SM59. In the "RFC Destinations" option, create a new RFC destination for your SAP system.
Step 5: Configure the Data Source in LogPoint
Finally, you need to configure the data source in LogPoint. To do this, go to the "Sources" tab in LogPoint and select "SAP" as the source type. Then, configure the data source by entering the RFC destination details and selecting the custom table for which you want to extract the modification logs.
In conclusion, extracting custom SAP table modification logs in SIEM using LogPoint requires some additional configuration steps. By following the steps outlined above, you can ensure that the logs are collected and analyzed properly, enabling you to detect and respond to potential security threats in your SAP system.
I hope you found this post helpful. If you have any questions or suggestions, please feel free to share them in the comments section below.
-
meaning of the "count() function"
Hi !
I would like to know a little more about the “count() function” in logpoint and it’s meaning. In fact as you can see in screen shot I received a log at 10:42:53 and count() is equal to 53 and theye are normaly 53 logs. But when I clic on this line (log) all of these 53 logs are exactly the same ! what is meaning ? How can I interpret ? Is it just one log (one action realised) ? or theye are really 53 logs (53 actions realised)
Thank you in advance for your help.
Best regards
Siawash
-
Webinar: Introducing Agent-X
Hi All,
We are excited to introduce AgentX , as a key native element of our Converged SIEM platform.
AgentX greatly helps to elevate threat detection, accelerate investigation, and ensures lightning-fast remediation while working seamlessly with SIEM and SOAR .
If you would like to hear more, join our upcoming webinar via the link below.
https://www.logpoint.com/en/webinars/agentx-webinar-endpoint-security/
-
Custom Layout Template in search Master?
Trying to create a custom layout template for a report for a client using the LPSM but unable to.
-
Excel Exports contain HTML encoding - How to avoid?
When exporting to Excel the field ‘msg’ contains the same HTML encoding as the GUI.
This is how some example data are shown in the GUI:

This is how the Excel Speadsheet looks like for the same data:
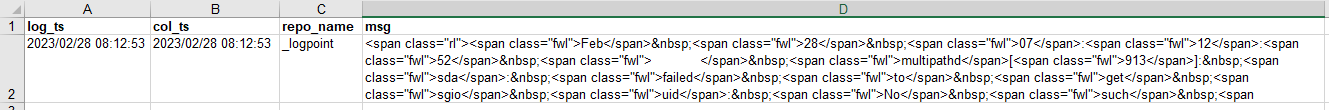
This is the sourcecode for the tabel in the GUI, which shows that it contain the same html <span> tags:

Is it possible to get the Excel Export without html encoding in the msg field?
Perhaps it could be an option to enable/disable html <tags> in exports in the preferences menu?
-
Gamaredon and their new “Gamma“ edition of malware TTPS
A year on since the first attack on Ukrainian territory and the unofficial beginning of the cyber war, the Secretary of Ukraine’s National Security and Defense Council, Oleksiy Danilov , has issued a warning that Russia could conduct a large-scale cyberattack as part of its renewed aggression. Through this updated edition of the Russia-Ukraine war, we look deeper into its execution, techniques they have deployed, the variations, and how we can utilize the capabilities of Logpoint Converged SIEM to detect, prevent and respond to attacks from Gamaredon and their new “Gamma“ edition of malware TTPS.
-
Exchange 2016/2019 onprem logging
Hi all,
What is the best way to ship Exchange onprem logs (OWA, SMTP and MSGTRK) to Logpoint?
The documentation is not very clear on this topic.
Thank you for your help.
Kind regards,
Dennis
-
Is LogPoint using LogPoint SIEM itself for their IT infrastructure?
I sometimes wonder if LogPoint (as a company) itself uses its own LogPoint SIEM to monitor its IT infrastructure (servers, clients, firewalls, etc.)? (see eating your own dog food principle)
I ask this because whenever it comes to user experience and serious functional errors in the software, I often have the feeling that only the support staff use the SIEM in their small virtualised test environments.
They then have only a few log sources connected (or pools and machine in the director environment), which means that some problems that only occur in very large environments do not appear at all.Two simple examples:
- If so many entries are to be displayed in the UI that a scrollbar becomes necessary, this is sometimes not implemented correctly or poorly in terms of UX.
- If the indexsearcher or other services simply crashes with "something is wrong" in the UI when running a search and do not deliver any further messages or hints and thus the entire service promise of a security provider is at stake.
I would guess that due to the short feedback loop within the company, many problems and bugs could be solved much faster if LogPoint had their own product in productive use.
LogPoint is soon at version 7.2 (!) and in some cases it is still not possible to guarantee that alert rules will run uninterruptedly without becoming obviously noticeable in the event of an error. I would expect this in early versions but not in 7 and onwards. I currently see the focus far too much on SOAR and other hyped gimmicks, while the base functionality of the SIEM is not working sufficiently.
-
Scanned ports
Hi !
I would like to know if it is possible to know hwo has scanned the sources ports and destinations ports ?
Thank you in advance :)
Best regards,
Siawash
-
A BOLDMOVE by the Chinese Hackers: Exploiting Fortinet Systems
Hi All,
We are excited to share our latest blog by Logpoint Security Researcher, Nilaa Maharjan.
In this piece, you can read about the zero-day vulnerability Fortinet disclosed in its FortiOS SSL-VPN products in December 2022, which was discovered to have been exploited by ransomware gangs.
Get research and analysis, insight, plus hints and tips, on how to mitigate BOLDMOVE with Logpoint in the blog below.
Link: https://www.logpoint.com/en/blog/boldmove-exploiting-fortinet-systems/
-
Enrich search results with the related data from a lookup table uploaded in Logpoint
Hi All,
We are happy to share that we have released a new version of our lookup plugin.
Lookup enriches logs with data from a Lookup table uploaded in Logpoint using CSVEnrichmentSource . You must install CSV Enrichment Source to upload the Lookup table.
Lookup supports the following process commands:
To learn more, please see the links below.
Release note: https://servicedesk.logpoint.com/hc/en-us/articles/9314493946525-Lookup
Documentation: https://docs.logpoint.com/docs/lookup-process-plugin/en/latest/
-
ChatGPT-SOAR integration now available for Logpoint
Hi All,
Have you tried our new ChatGPT-SOAR integration yet? The OpenAI Actions will allow you to ask ChatGPT anything and incorporate the responses into your playbooks and use cases. The actions require valid credentials you can apply for at platform.openai.com/signup. The actions allow you to send requests, receive answers and modify the model used for receiving results.
To read more about the use cases: https://www.logpoint.com/en/media-room/#/pressreleases/logpoint-makes-chatgpt-soar-integration-available-3232134
To download: https://servicedesk.logpoint.com/hc/en-us/articles/9183395790237-ChatGPT-Integration
-
Utilizing Network Logs for Investigation and Remediation to uncover illegitimate Crypto-Mining Activity (Cryptojacking)
Crypto-mining has become a growing threat in recent years with more than 500,000 individuals affected only in 2022 according to Kaspersky reports. Typically using processing power of the victim’s computer illicitly to mine cryptocurrency, allowing cybercriminals to remain hidden for months.
In our newest piece by Logpoint blackbelt , Swachchhanda Shrawan Poudel you can read about the best practices and tips&tricks to detect and remediate illegitimate Crypto-Mining Activity with Logpoint.
Read the full article on the link below:
https://www.logpoint.com/en/blog/uncovering-illegitimate-crypto-mining-activity/
-
Public release of GoogleCloudPlatform v.6.0.0.
Hi All,
We are excited to share the release of GoogleCloudPlatform v.6.0.0.
Google Cloud Platform (GCP) is a suite of cloud computing services that provides infrastructure as a service, platform as a service and serverless computing environments.
Alongside a set of management tools, it offers a series of modular cloud services including computing, data storage, data analytics and big data processing.
To read more on this release, please follow the link below:
https://servicedesk.logpoint.com/hc/en-us/articles/8956510332061
User groups in Zendesk Community allow members to connect, share insights, ask questions, and collaborate within specific interest areas.